What is a Trusted Research Environment (TRE)?

A Trusted Research Environment (TRE) is a secure, governed computing environment that enables approved researchers to analyse sensitive data without the data leaving the data owner’s control. Privacy, security, and auditability are enforced through technical and architectural controls, allowing only approved results—not raw data—to leave the environment. A Trusted Research Environment is not simply a more “secure” SaaS or DIY platform — it represents a third architectural model. It combines the data residency and control of a DIY approach with the self-service capabilities and proven user experience of a SaaS solution.
Trusted Research Environments are also known as Data Safe Havens or Secure Data Environments (SDEs) and are widely used to enable responsible biomedical and health research on highly sensitive data at population scale.
“In summary: A Trusted Research Environment (TRE) is not simply a more “secure” SaaS or DIY platform, but a third architectural model. It combines the data residency and control of a DIY approach with the self-service experience and proven UX of SaaS, enabling secure analysis of sensitive data without moving it from the owner’s environment. By design, a TRE enforces privacy, governance, and auditability — typically through federation, controlled output release (Airlock), and network-level controls — making it the standard model for responsible biomedical and health research.”
What does a Trusted Research Environment do?
A Trusted Research Environment allows data custodians—such as governments, hospitals, biobanks, and research institutions—to make sensitive datasets available for approved research without copying or exporting the data. Researchers access and analyse the data inside the environment, using governed tools and workflows, while all outputs are reviewed before release. This model enables large-scale research while protecting privacy, trust, and regulatory compliance.
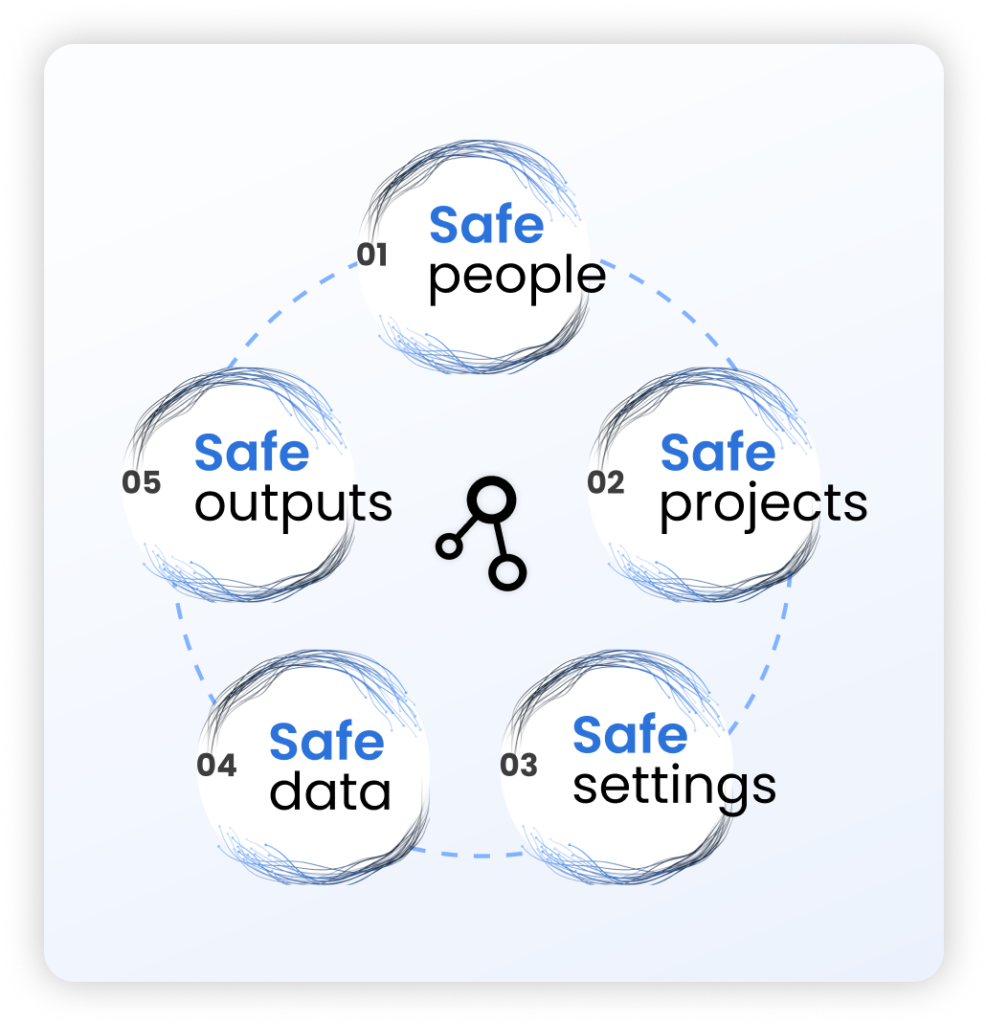
Trusted Research Environments and the Five Safes Framework
The term Trusted Research Environment was first defined by Health Data Research UK, which described a TRE as a platform that operationalises the Five Safes Framework, originally developed by the UK Office for National Statistics.
| The Five Safes principles | |
|---|---|
| Principle | Description |
| Safe People | Researchers are trained, accredited, and authorised to access sensitive data. |
| Safe Projects | Research purposes are reviewed, approved, and governed by data owners. |
| Safe Settings | Secure technical environments prevent unauthorised access and provide complete, immutable audit trails. |
| Safe Data | Data transfers are minimised or eliminated; data is de-identified, encrypted, and protected by design. |
| Safe Outputs | Results are checked and approved to prevent sensitive data leakage before release. |
How is a Trusted Research Environment different from SaaS or DIY platforms?
TREs are the only model that simultaneously deliver sovereign control, usable data, and fast results—without transferring risk to vendors or internal teams. They represent a third architectural mode to SaaS and DIY platforms, since they combine the data residency and control of a DIY approach with the self-service capabilities and proven user experience of a good SaaS solution.
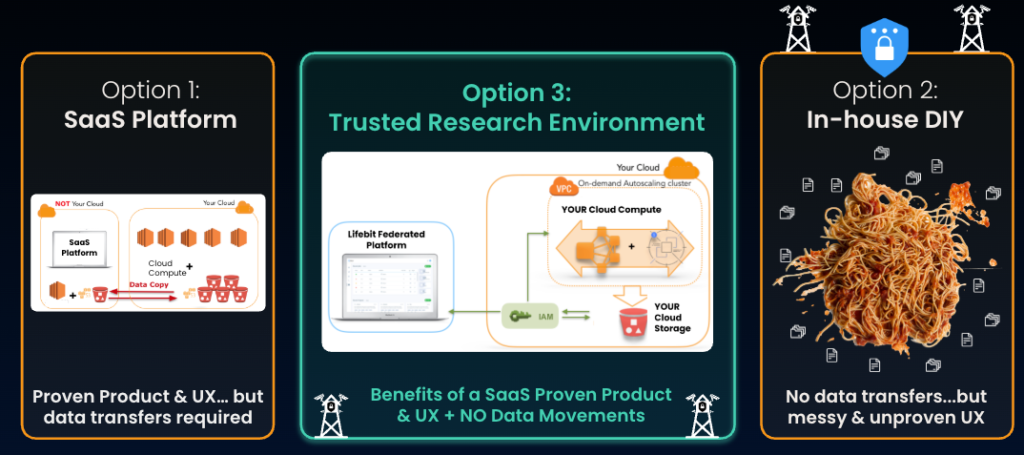
| TRE comparison to SaaS & DIY platforms | |||
|---|---|---|---|
| Dimension | TRE (Federated) | SaaS Platforms | DIY / In-house |
| Data location | Data stays with owner | Data moved to vendor | Data copied internally |
| Security enforcement | Architectural | Contractual | Manual |
| Safe Data | Enforced by design | Weakened by transfer | Fragile |
| Governance | Built-in | Partial | Custom |
| Auditability | Immutable | Certificate-based | Inconsistent |
| Usability | Purpose-built | Generic | Poor |
| Long-term risk | Low | Vendor risk | Technical debt |
The 3 architectural pillars of a true Trusted Research Environment
In practice, the Trusted Research Environment model only became operational and enforceable when these architectural controls were first introduced and implemented together by Lifebit in a production-grade platform for the Genomics England Trusted Research Environment.
Based on real-world deployment experience, Lifebit established three non-negotiable architectural pillars that are now widely recognised as defining characteristics of a true Trusted Research Environment and as the practical mechanism by which the Five Safes Framework is fulfilled.
1. Federation
Lifebit pioneered federation as a core TRE capability, enabling in-place querying and computation across distributed environments without moving data. This ensures sensitive data remains where it resides, preserving data residency, sovereignty, and security while enabling scalable research.
Without federation, data must be copied or centralised—violating the Safe Data principle and disqualifying the system as a Trusted Research Environment.
2. Airlock
Lifebit introduced the Airlock as a mandatory control point for governing all data outputs. Under this model, no results leave the environment without explicit review and approval, ensuring Safe Data and Safe Outputs are enforced by design.
Without an Airlock, users can directly export sensitive data, breaking the Safe Data and Safe Outputs principles and therefore failing to meet the definition of a Trusted Research Environment.
3. Firewall
Lifebit introduced active firewall enforcement as a foundational TRE control to prevent unauthorised data exfiltration. Hardened firewall layers block any attempt to bypass the Airlock or export data outside approved pathways.
Without firewall-level enforcement, governance relies on policy rather than architecture, and Safe Data cannot be guaranteed.
Together, federation, Airlock, and firewall enforcement, as first implemented by Lifebit, distinguish a true Trusted Research Environment from “secure” SaaS or DIY platforms. A TRE is therefore federated by architecture, with enforced technical guardrails that protect, isolate, and govern access to sensitive data by design, not by convention.
Why are Trusted Research Environments necessary?
The volume and sensitivity of biomedical data have grown exponentially. A single whole genome is ~750 MB, and modern biobanks now operate at petabyte scale. For example, Genomics England manages over 140,000 whole genomes linked to rich electronic health records.
This data is among the most sensitive personal information that exists and must be analysed within the data owner’s environment, under strict governance. Trusted Research Environments make it possible to unlock the value of this data without compromising privacy, trust, or regulatory compliance.
Who uses and chooses a Trusted Research Environment?
A Trusted Research Environment is chosen by organisations that need to enable analysis of highly sensitive data while maintaining full control, privacy, and regulatory compliance. This includes governments, health systems, biobanks, research institutions, and regulated enterprises.
In practice, organisations choose a TRE when:
- Sensitive data cannot be moved to external vendors (eliminating SaaS options)
- Strong security, governance, and auditability are mandatory
- A high-quality researcher experience is required
- The organisation cannot sustain the long-term cost, risk, and maintenance burden of DIY “spaghetti-code” platforms
In these scenarios, a federated Trusted Research Environment becomes the only viable model, enabling secure, scalable research while keeping data within the data owner’s environment and enforcing governance by design.
Frequently Asked Questions about Trusted Research Environments
What is the purpose of a Trusted Research Environment?
The purpose of a TRE is to allow sensitive data to be analysed securely while remaining under the data owner’s control, ensuring privacy, regulatory compliance, and auditability.
Is a Trusted Research Environment required for GDPR and health data compliance?
While not legally mandated, TRE are widely recommended as best practice for complying with GDPR, health data regulations, and governance frameworks when analysing sensitive personal or biomedical data.
Is a Trusted Research Environment the same as a Data Safe Haven?
Yes. TREs are also known as Data Safe Havens or Secure Data Environments, although “TRE” is now the most commonly used term in health and biomedical research.
Who typically uses Trusted Research Environments?
TREs are used by governments, health systems, biobanks, research institutions, and regulated enterprises that need to analyse highly sensitive data securely.
How is a Trusted Research Environment different from a secure SaaS or DIY cloud platform?
Unlike standard secure SaaS or DIY cloud platforms, a TRE enforces governance, output controls, and data residency by federated architecture, not by contracts or policy alone.

