Trusted Research Environments 101

Open uping Research Potential with Secure Data Access
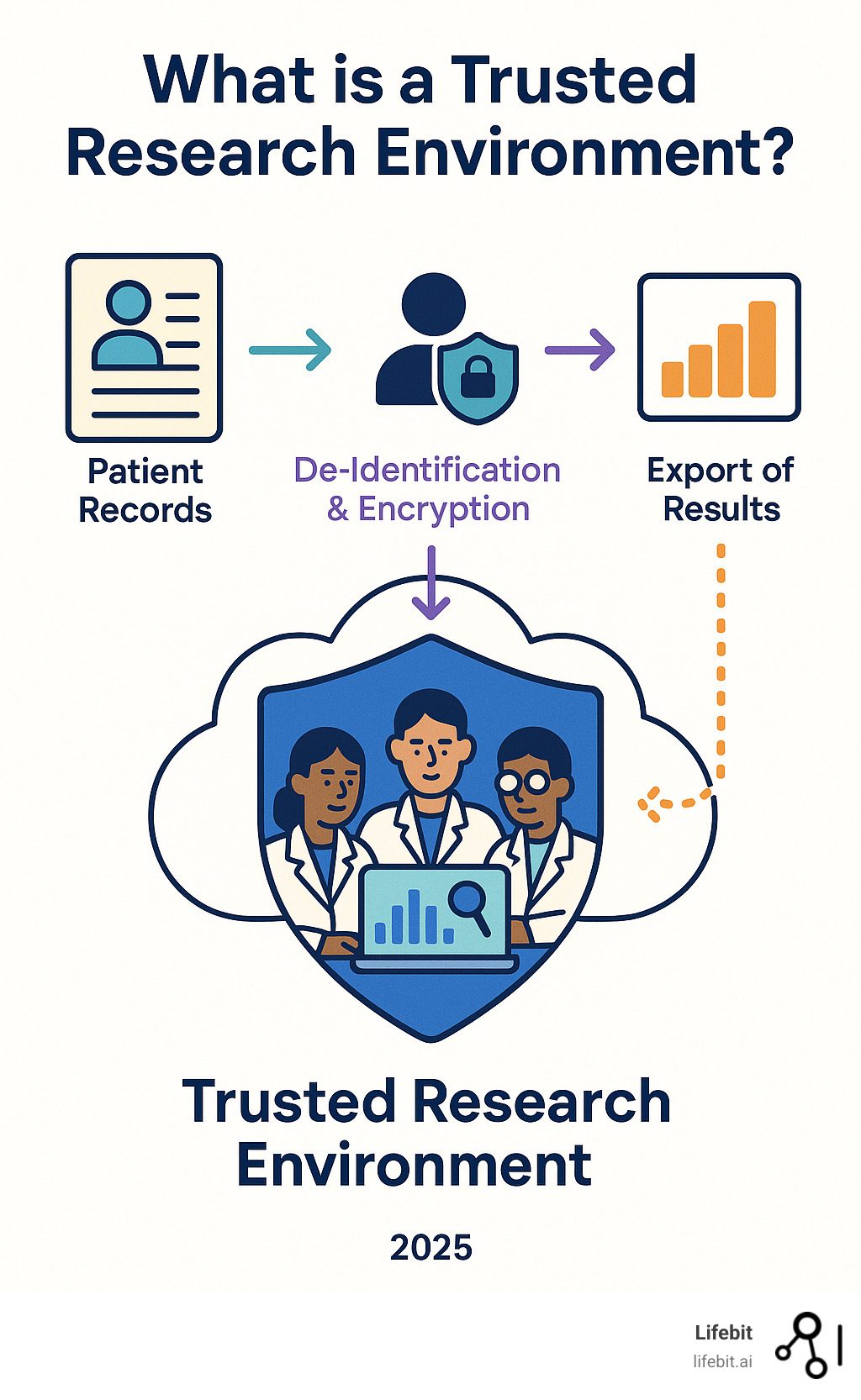
What is a Trusted Research Environment? A Trusted Research Environment (TRE) is a highly secure computing environment that allows approved researchers to analyze sensitive data remotely without the data ever leaving. Also known as Data Safe Havens or Secure Data Environments, TREs are defined by key characteristics:
- Secure Access: Only vetted researchers can enter.
- Data Protection: Information never leaves the environment.
- Remote Analysis: Researchers work with data from anywhere.
- Controlled Outputs: Only approved, non-identifying results can be exported.
The need for TREs is critical. Modern biomedical research relies on massive datasets, from electronic health records to genomic databases with over 135,000 whole genomes. However, this data is often trapped in institutional silos.
Traditional data sharing is slow and risky, with data access approvals taking six months or longer and moving patient data creating security concerns. TREs solve this by bringing researchers to the data, not the other way around. This protects patient privacy while enabling the large-scale studies needed to advance public health.
As Maria Chatzou Dunford, CEO and Co-founder of Lifebit, I’ve seen how TREs can transform research while upholding the highest standards of data protection. These environments are essential for open uping the full potential of health data.
Easy What is a Trusted Research Environment? glossary:
What is a Trusted Research Environment (TRE)?
A Trusted Research Environment is a digital fortress designed to safeguard sensitive data for research. Also known as a Secure Data Environment (SDE) or Data Safe Haven, its primary goal is to bring researchers to the data, rather than moving data to researchers. Instead of copying and distributing vast, sensitive datasets, which increases risk, a TRE creates a secure space where data resides permanently. Researchers access this space remotely to perform analysis, ensuring patient privacy and robust data security.
This model is vital for large-scale datasets, such as the petabytes of genomic and health data managed by biobanks like Genomics England, which houses over 135,000 whole genomes. TREs overcome the institutional silos and slow approval times (often six months or longer) that hinder traditional research, accelerating findy while maintaining trust.
For more information on the concept of a secure research environment, you can explore our detailed guide: More info about a Secure Research Environment.
The Core Components of a TRE
A robust Trusted Research Environment is built on a foundation of technical and governance controls.
Technical Controls:
- Secure Access Control: Ensures only approved individuals can enter, using methods like two-factor authentication and role-based access controls (RBAC).
- Data Encryption: All data is encrypted, both at-rest (in storage) and in-transit (while being moved), making it unreadable to unauthorized parties.
- Secure Analytical Tools: Provides a suite of pre-approved tools (e.g., RStudio, Jupyter Notebooks) to prevent installation of malicious software and control data flow.
- Auditing and Monitoring: Logs and monitors every action within the TRE to detect suspicious activity.
- Incident Response: Establishes clear plans to respond to security incidents and recover data to ensure research continuity.
Governance Controls:
- Data Access Committees (DACs): Independent bodies that review and approve research projects based on ethical guidelines and public benefit.
- Public and Patient Involvement (PPI): Engages the public in discussions about data use to build trust and ensure research aligns with societal values.
- Compliance Frameworks: Adheres to data protection regulations like GDPR and HIPAA, providing a legally sound framework for research.
To learn more about these essential elements, explore our insights on the Key Features of a Trusted Research Environment.
The Challenges TREs Overcome
Before TREs, research with sensitive data faced significant problems that slowed or prevented scientific advancement.
- Data Segregation: Health data was often locked in institutional silos, making it difficult to combine for large, powerful studies.
- Security Risks: Copying and transferring sensitive datasets created multiple vulnerabilities, increasing the risk of data breaches.
- Regulatory Problems: Complying with data protection laws like GDPR and HIPAA was a complex, slow process that created bottlenecks.
- Research Inefficiency: The combination of slow approvals, security risks, and data silos created immense collaboration barriers and stifled innovation.
What is a Trusted Research Environment? It is the solution to these problems. By providing centralized, secure access, TREs reduce breach risks, streamline compliance, and break down data silos to accelerate research.
Find more about how TREs address these issues and improve the research process: Advantages of Trusted Research Environments.
The Five Safes: A Framework for Trustworthy Data Access

To ensure data is secure and private within a Trusted Research Environment, we use the ‘Five Safes’ framework. This internationally recognized standard, developed by the UK Office for National Statistics, is a best practice for managing data access responsibly. It provides a comprehensive checklist for building trust with data custodians and the public by ensuring every step of the research process is rigorously controlled.
For a deeper dive, you can refer to: The Five Safes Framework explained. We’ve also explored its role here: Preserving Patient Data Privacy and Security.
Safe People
This principle ensures that only trustworthy and capable individuals can access sensitive data. Researchers must be trained in data privacy and ethics, formally vetted through accreditation, and held to clear accountability through signed agreements. User accreditation ensures they receive the minimum access necessary for their approved project.
Safe Projects
This focuses on what kind of research is permitted. Every project must gain ethical approval from an independent committee and demonstrate a clear public benefit. Research proposals must have defined research questions to justify the need for data access. Formal systems like the UK’s Data Access Request Service (DARS) ensure these approvals are consistent and transparent.
Safe Settings
This refers to the secure environment where data is analyzed—the TRE itself. It relies on secure infrastructure with robust cybersecurity measures like firewalls and intrusion detection. Strict access controls, such as disabled internet or copy/paste functions, are implemented for preventing unauthorized data removal. For highly sensitive data, this may even involve physical secure labs.
Safe Data
This addresses the data itself, which is treated to minimize re-identification risk. This involves de-identification (removing direct identifiers), anonymization, and pseudonymization (replacing identifiers with codes). The principle of data minimization is also applied, providing only the data absolutely necessary for the research, protecting patient confidentiality.
Safe Outputs
This ensures that only non-identifiable, approved results can leave the TRE. Raw data never exits. All outputs undergo statistical disclosure control to check that no individual can be identified from the results. This process of checking results before release is critical for preventing re-identification. Only aggregated results are typically allowed out, and even code is reviewed before export.
The Transformative Impact of TREs on Research
The impact of a Trusted Research Environment on modern research has been revolutionary, shifting from isolated data islands to a connected ecosystem for findy. By enabling secure access to vast datasets, TREs accelerate research timelines, leading to faster public health breakthroughs and data-driven findings that were previously impossible.
Researchers from different continents can now collaborate on the same sensitive datasets in real-time, all within secure environments that protect patient privacy.
Why is a Trusted Research Environment a Game-Changer for Collaboration?
TREs are a game-changer because they break down data silos. They enable multi-institutional studies that were once plagued by logistical and security problems. In the UK, for example, 15 major UK TREs have collaborated on research projects, creating a powerful network of interconnected capabilities. This model fosters the sharing of code and methods, which improves scientific reproducibility. The efficiency gains are immense, allowing researchers to focus on analysis rather than data access negotiations. This was demonstrated by a population-based cohort study of 46 million adults conducted using TRE infrastructure—a scale unachievable with traditional methods.
For more insights into how TREs are changing research workflows, explore our detailed analysis: Research Efficiency with Trusted Research Environments.
Real-World Examples of TREs in Action
The power of TREs is evident in how they are used to tackle real-world health challenges.
- UK Biobank: With data from over 500,000 participants, its TRE is a global resource for health research, enabling thousands of studies on diseases from cancer to dementia.
- Genomics England: Its Research Environment, housing over 135,000 whole genomes, has accelerated findies in rare diseases and cancer while ensuring patient confidentiality. Learn more at Genomics England.
- COVID-19 Pandemic Response: The NHS Digital TRE was critical for understanding the virus. It enabled researchers to analyze de-identified health data from millions of patients in near real-time. One landmark study of over 46 million adults in England provided crucial insights that informed global public health policy, showcasing the rapid response capabilities of TREs.
These examples illustrate how TREs make entirely new types of research possible, combining scale, security, and collaboration to transform medicine.
To explore more examples of how TREs are driving medical breakthroughs, visit: Accelerating Disease Research with Trusted Research Environments.
The Future of Research: Evolving TREs and Emerging Trends

The journey of What is a Trusted Research Environment? is constantly advancing, driven by technological leaps and policy shifts. The future promises more connected and powerful TREs designed to meet the demands of next-generation research, driven by growing data complexity, advanced AI, and the global push for interoperability.
What is a Trusted Research Environment’s Role in Federated Learning?
Federated learning is a breakthrough approach for analyzing data across multiple locations without centralizing it. Instead of moving data, the analysis algorithms are sent to the data within each secure TRE. Only aggregated, non-sensitive results are shared, meaning the raw data never leaves its secure home.
This method offers huge benefits: no data movement, which improves security; access to diverse global data that cannot be pooled; and massive scalability. While not yet standard, federated analysis is the next frontier for large-scale, privacy-first collaborative research.
To explore more about this cutting-edge approach, dive into our insights on: Federated Trusted Research Environment.
Integrating AI, Machine Learning, and Advanced Analytics
AI and Machine Learning (ML) are essential for analyzing today’s massive biomedical datasets. A Trusted Research Environment provides the secure playground needed to train and deploy these powerful tools on sensitive data.
Modern TREs are evolving to offer:
- Secure Sandbox for AI/ML: Allows researchers to train models on sensitive data without it ever leaving the secure space.
- Training Complex Models: Provides powerful computational resources (HPC, GPUs) needed for demanding AI/ML tasks.
- Real-time Analytics: Enables analysis of dynamic data streams for applications like disease surveillance.
- Software Development: Supports the entire research lifecycle with integrated tools for building and managing code.
The potential for TREs to accelerate AI-driven findy is enormous, with emerging privacy-preserving techniques making these environments even more secure.
For a deeper look into how advanced analytics are being brought into these secure environments, check out our article on: Data Analysis in Trusted Research Environments.
The Evolving Regulatory and Policy Landscape
As TRE technology evolves, so do the rules governing its use. Governments worldwide recognize that secure data environments are vital for open uping the value of health data while maintaining public trust.
Key policy shifts include:
- The Goldacre Review: This influential 2022 UK report recommended TREs become the standard for analyzing NHS patient data, driving their adoption and standardization. Read the report: The Goldacre Review.
- Standardization and Interoperability: Initiatives like the DARE UK programme are creating national frameworks to help different TREs work together, breaking down data silos.
- Public Trust and Transparency: Regulators are emphasizing public involvement and clear communication about how data is protected and used for public benefit.
- International Collaboration: Policies are adapting to support global research, addressing cross-border data protection laws like GDPR and HIPAA.
These efforts are shaping a future where TREs form a connected global research network operating under high, consistent standards for security and ethics.
Frequently Asked Questions about Trusted Research Environments
Here are answers to some of the most common questions about how a Trusted Research Environment works.
What is the difference between a TRE and a standard cloud database?
A standard cloud database is designed for secure storage and retrieval. A Trusted Research Environment is a purpose-built analytical environment that adds multiple layers of security and governance on top of secure storage. While a database stores data, a TRE provides a controlled space for its analysis.
A TRE wraps data in a comprehensive security blanket that includes advanced encryption, network segmentation, and intrusion detection. Crucially, it is governed by strict ethical guidelines and the Five Safes framework. This includes oversight from Data Access Committees and granular access controls to ensure only approved researchers can conduct approved projects. A cloud database offers storage; a TRE offers a secure, compliant, and controlled environment for sensitive research.
Can researchers take data out of a TRE?
No, researchers cannot take raw, sensitive data out of a Trusted Research Environment. This is a core security principle. Researchers work with the data remotely within the TRE’s secure boundaries.
Only approved, non-disclosive results (like aggregated statistics or charts) can be exported. These outputs undergo strict disclosure control checks to ensure no individual can be re-identified. This ‘Safe Outputs’ principle is fundamental to protecting patient privacy while enabling research.
Who decides who gets access to the data in a TRE?
Access is decided by an independent oversight group, typically called a Data Access Committee (DAC). This committee is composed of experts in data governance, ethics, and research, and often includes public and patient representatives to ensure decisions align with societal values.
The DAC uses the ‘Safe People’ and ‘Safe Projects’ principles to make decisions. They vet researchers to ensure they are accredited and trustworthy. They also evaluate each research proposal for its ethical soundness, scientific merit, and public benefit, ensuring data is used responsibly and for the greater good.
Conclusion: Building a Secure Future for Data-Driven Research
Exploring what a Trusted Research Environment is reveals its vital role in modern science. TREs strike a crucial balance, open uping the potential of sensitive data for breakthroughs while upholding the highest standards of privacy and security. By bringing researchers to the data and applying the ‘Five Safes’ framework, TREs accelerate research, enable global collaboration, and build the public trust essential for data-driven findy.
The future of research is collaborative and federated. At Lifebit, we are committed to powering this secure ecosystem. Our next-generation federated AI platform, with its Trusted Research Environment (TRE), Trusted Data Lakehouse (TDL), and R.E.A.L. (Real-time Evidence & Analytics Layer), is designed for these evolving needs. We empower researchers to make groundbreaking findies and enable secure collaboration across data environments, from London to New York and across five continents, building a future where data works for humanity, safely and responsibly.
Ready to see how we’re building this secure future for data-driven research?
Find Lifebit’s next-generation Trusted Research Environment.


6 thoughts on “Trusted Research Environments 101”
Comments are closed.