HIPAA-Compliant Analytics: Crunch Numbers, Not Compliance Rules

HIPAA-compliant data analytics: Secure 2025
Why HIPAA-Compliant Data Analytics Matters More Than Ever
HIPAA-compliant data analytics is the gold standard for deriving insights from patient data while upholding strict privacy. Key requirements include executing Business Associate Agreements (BAAs) with all vendors, robust data encryption, strict access controls, comprehensive audit trails, and de-identification techniques.
The stakes are enormous. Healthcare data breaches cost an average of $10.1 million in 2022, and HIPAA fines can reach $1.5 million per violation category annually. Despite this, many healthcare websites still transmit user data to third parties, creating significant compliance risks.
The challenge is extracting insights from sensitive data without violating federal law. The solution lies in choosing the right analytics strategy, whether self-hosting, using trusted partners, or leveraging specialized platforms built for compliance.
I’m Maria Chatzou Dunford, CEO and Co-founder of Lifebit. We build secure, federated platforms for biomedical data analysis. My experience has shown that correctly implemented HIPAA-compliant data analytics is essential for accelerating drug findy and improving patient outcomes.
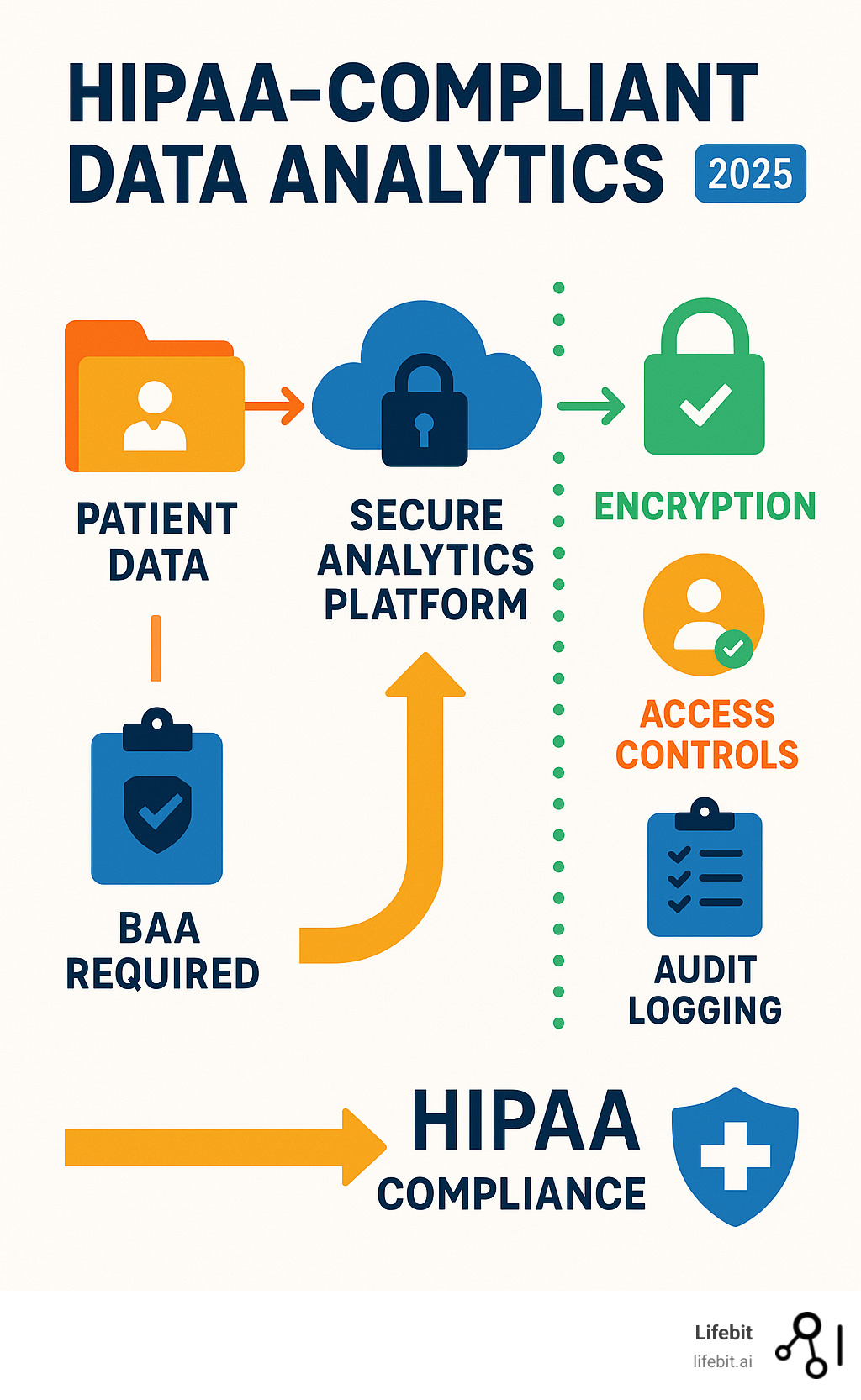
HIPAA-compliant data analytics vocab explained:
The Intersection of HIPAA and Data Analytics
Understanding HIPAA-compliant data analytics requires knowing how federal privacy laws impact healthcare technology. The Health Insurance Portability and Accountability Act of 1996 (HIPAA) was created to protect patient privacy and build the trust necessary for innovation.
HIPAA governs who can access and use patient data and what safeguards are required. This is critical for analytics, which often involves highly sensitive health histories. The law applies to Covered Entities (providers, health plans) and their Business Associates (vendors, including analytics providers, who handle patient data on their behalf).
Healthcare data analytics uses insights from EHRs, clinical trials, and claims data to improve care. Every use of patient data must meet HIPAA’s strict standards, with the goal of Preserving Patient Data Privacy and Security while open uping its potential.
What is Protected Health Information (PHI)?
Protected Health Information (PHI) is any health data that can be linked to a specific person. When it’s electronic, it’s called ePHI. HIPAA identifies 18 specific identifiers that can turn seemingly anonymous data into PHI, making robust technical safeguards essential.
The 18 PHI identifiers include:
- Names
- Geographic information smaller than a state
- Dates related to individuals (except year)
- Phone and fax numbers
- Email addresses
- Social Security numbers
- Medical record numbers
- Health plan beneficiary numbers
- Account numbers
- Certificate and license numbers
- Vehicle identifiers and license plates
- Device identifiers and serial numbers
- Web URLs
- IP addresses
- Biometric identifiers
- Photographs
- Any other unique identifying numbers or codes
Notably, IP addresses and device IDs are on this list. This means web analytics from a patient portal or tracking pixels on a healthcare website can create PHI, requiring the same protection as traditional medical records.
Why HIPAA Compliance is Crucial for Analytics
HIPAA-compliant data analytics is about more than avoiding fines; it’s about enabling responsible innovation. Patient trust is the foundation. When patients know their data is protected, they are more willing to share it, fueling medical breakthroughs.
The financial stakes are huge. Data breach costs in healthcare are the highest of any industry, averaging $10.1 million in 2022. The reputational damage from a violation can last for years, impacting patient loyalty and recruitment. Conversely, strong compliance practices often improve operational efficiency by creating more secure, reliable, and manageable systems. Responsible innovation begins where HIPAA and analytics intersect. You can explore More about Data Security in Nonprofit Health Research to see how these principles apply in research contexts.
Key Risks and Challenges in Healthcare Analytics

Building HIPAA-compliant data analytics systems means navigating significant risks. The biggest challenges include privacy breaches from cyberattacks or human error, unauthorized access by internal staff, and third-party vendor risk from partners who may not have adequate safeguards. These risks are not theoretical; they manifest in costly data breaches that erode patient trust and attract regulatory scrutiny. Common attack vectors include phishing campaigns targeting employees with access to PHI, ransomware that encrypts critical patient data, and insider threats, whether malicious or accidental.
Marketing compliance has also become a major hurdle. Traditional digital marketing tactics like user tracking and retargeting often don’t work in healthcare, as the data collected can easily become PHI and require protection under the full weight of HIPAA.
Penalties for Non-Compliance
HIPAA violations have severe financial consequences, enforced by the HHS Office for Civil Rights (OCR). Fines are tiered based on the organization’s level of culpability, reflecting whether the violation was accidental or a result of willful neglect.
The Four Tiers of HIPAA Penalties:
- Lack of Knowledge: The organization was unaware of the violation and could not have realistically known. Fines range from $100 to $50,000 per violation.
- Reasonable Cause: The organization knew or should have known about the violation but did not act with willful neglect. Fines range from $1,000 to $50,000 per violation.
- Willful Neglect—Corrected: The violation was intentional or resulted from conscious disregard, but the organization corrected it within 30 days. Fines range from $10,000 to $50,000 per violation.
- Willful Neglect—Not Corrected: The violation was intentional, and the organization made no effort to correct it. This carries the highest penalty of at least $50,000 per violation.
These fines can accumulate rapidly, with an annual maximum of $1.5 million per violation category. For example, a single stolen, unencrypted laptop could represent a violation for every patient record it contained. Beyond federal fines, organizations face civil action lawsuits from affected patients and enforcement actions from state attorneys general. In extreme cases of knowing and wrongful disclosure of PHI, individuals can face criminal charges, including imprisonment. Regulators also impose costly corrective action plans that require years of monitored oversight to implement. For real-world examples, see these details on compliance violations and major settlements, such as the $16 million fine paid by Anthem Inc. after a massive data breach.
The Impact on Healthcare Marketing and Advertising
Modern marketing practices pose serious compliance risks in healthcare. Online tracking technologies, such as analytics tools and social media pixels, can create PHI when a user interacts with health-specific content. This makes activities like retargeting campaigns based on visits to an oncology page a potential violation.
Unlike other industries, healthcare requires specific patient authorization for most marketing uses of PHI. A generic consent in a website’s terms and conditions is insufficient. Valid authorization must be a separate, detailed document that specifies exactly what PHI will be used, for what purpose, who will receive it, and for how long. Mapping the user journey is also complex, as every digital touchpoint—from a symptom checker to an appointment scheduling form—could involve protected data. Traditional marketing tools must be re-evaluated in light of these HIPAA privacy regulations.
The Challenge of Online Tracking Pixels
Tools like the Meta Pixel or Google Ads conversion trackers are particularly problematic. When a user visits a hospital’s webpage about a specific, sensitive health condition (e.g., HIV treatment, addiction recovery), the tracking pixel can capture their IP address (a HIPAA identifier) and transmit it to the third-party ad platform along with the context of the page visit. This combination of data can constitute PHI, as it links an identifiable individual to a specific health interest or condition. Because vendors like Meta and Google typically do not sign BAAs for these standard advertising services, transmitting this data is a direct violation of HIPAA. This has led to numerous class-action lawsuits and intense regulatory focus, forcing healthcare organizations to either remove these trackers or implement sophisticated consent management and data filtering solutions.
A Practical Guide to Achieving HIPAA-Compliant Data Analytics

Achieving HIPAA-compliant data analytics requires building a culture of privacy, not just checking boxes. This starts with a comprehensive risk analysis to identify where PHI lives across all systems and where vulnerabilities exist. This is followed by establishing robust data governance with clear, documented policies for data collection, use, retention, and disposal. These policies should form the foundation of your compliance program.
Effective, ongoing staff training is crucial, as even the best systems can be undermined by human error. Employees must understand their role in protecting PHI. Finally, a detailed and tested incident response plan ensures you can react quickly and effectively if a breach occurs, minimizing harm, meeting notification deadlines, and demonstrating due diligence to regulators.
The Role of a Business Associate Agreement (BAA)
A Business Associate Agreement (BAA) is a non-negotiable contract with any third-party vendor that handles PHI on your behalf. It’s a legally binding promise that your vendor will protect patient data to the same standard you do. A BAA establishes vendor liability, sharing the responsibility if a breach occurs on their end. Without a signed BAA in place before any PHI is shared, the covered entity is in violation of HIPAA.
Before signing, it is critical to perform due diligence on the vendor to ensure they have the technical and administrative capacity to meet their obligations. This includes reviewing their security policies, certifications (like SOC 2 or HITRUST), and data breach history. The agreement’s contract requirements must specify how the vendor can use PHI and what security measures they must have. It also outlines data protection duties and breach notification protocols, ensuring you are informed quickly if an incident occurs. You can find Sample Business Associate Agreement provisions to ensure your contracts are comprehensive. Key clauses should cover permitted uses, subcontractor obligations (ensuring they also sign BAAs), data return/destruction upon termination, and audit rights.
Data De-Identification and Anonymization Techniques
One of the smartest strategies for HIPAA-compliant data analytics is to de-identify data by removing personal identifiers. Once data is properly de-identified, it is no longer considered PHI and can be used for analytics, research, and other purposes without the same strict HIPAA constraints. This allows you to analyze patterns and trends without exposing individual identities.
HIPAA provides two methods for this:
- The Safe Harbor Method: This is a prescriptive approach that involves removing all 18 specific identifiers of the individual and of their relatives, employers, or household members. These identifiers include names, all geographic subdivisions smaller than a state, all elements of dates (except year) directly related to an individual, telephone numbers, email addresses, Social Security numbers, medical record numbers, IP addresses, biometric identifiers, full-face photos, and any other unique identifying number, characteristic, or code.
- The Expert Determination Method: This is a more flexible, principles-based method. It allows a qualified statistician or data scientist to apply statistical or scientific principles to determine that the risk of re-identifying an individual from the data is “very small.” The expert must document their methodology and conclusion, which provides the covered entity with a formal basis for treating the data as de-identified. This method is often preferred when more data granularity is needed for analysis, as it may allow for the retention of certain data points that Safe Harbor would require removing.
Both methods focus on removing identifiers and mitigating risk. While true, perfect anonymization is complex, de-identification is a powerful tool for enabling research while staying within HIPAA’s boundaries. Exploring More on Secure Data Environments for Healthcare Research can provide valuable insights into these processes.
Pseudonymization: A Related but Distinct Concept
Pseudonymization is the process of replacing direct identifiers with a reversible, consistent token or “pseudonym.” For example, a patient’s name might be replaced with a random alphanumeric string. While this is a valuable security measure that reduces risk, pseudonymized data is still considered PHI under HIPAA. This is because the organization holds the key to re-link the pseudonym to the individual’s identity. Therefore, pseudonymization alone does not remove the data from HIPAA’s scope, but it is a best practice for securing PHI within a compliant environment.
Choosing Your Analytics Strategy: Key Approaches

When implementing HIPAA-compliant data analytics, you face a key decision: build your own secure system or partner with a managed service. The right choice depends on your organization’s needs, weighing factors like data control, security liability, scalability, and cost.
The Self-Hosted Approach for Maximum Control
Self-hosting, whether on-premise or in a self-managed cloud, gives you complete control over your data. This full data ownership is a major advantage for organizations with strict data residency rules or highly sensitive research. However, it demands significant internal expertise in cybersecurity, infrastructure, and HIPAA regulations. With this approach, all responsibility for compliance and security rests on your shoulders. For more on this, see our guide on self-hosted compliance best practices.
Using Trusted Partners for HIPAA-Compliant Data Analytics
Partnering with specialized vendors often provides the best balance of security and practicality. These cloud-based solutions offer enterprise-grade security that is expensive to build in-house. Under a shared responsibility model, the vendor manages platform security while you manage user access and configuration. Vetting partners is critical; look for proven track records and certifications. The non-negotiable requirement is the execution of a comprehensive Business Associate Agreement (BAA).
Leveraging Data Governance Platforms for Healthcare
Regardless of your hosting choice, a modern data governance platform adds an intelligent layer of protection. These platforms offer data filtering to block PHI from reaching non-compliant tools and secure data routing to ensure information only travels through approved channels. At Lifebit, our federated platform is built on these principles. It allows organizations to analyze global biomedical data while maintaining strict privacy controls, simplifying compliance challenges while expanding analytical capabilities. Explore Lifebit’s healthcare privacy platform to see how this works in practice.
Navigating the HHS Guidance on Online Tracking Technologies
The use of online tracking technologies in healthcare is a complex and evolving area. In late 2022, HHS issued guidance stating that tracking tools must comply with HIPAA when used by covered entities, even on public-facing web pages. This caused significant industry pushback, leading to a 2024 court ruling that HHS had overstepped its authority in how it framed the guidance.
However, this ruling does not eliminate the need to protect PHI in analytics. The core principle remains: if tracking technologies collect or transmit PHI, they must be HIPAA-compliant. The challenge is that data like an IP address, when combined with a visit to a health-specific page, can be considered PHI. Organizations must carefully assess all tracking tools, ensure BAAs are in place where necessary, and obtain patient authorization for marketing uses of PHI. The official HHS guidance on online tracking technologies provides full details, though the legal landscape continues to shift. For more on secure environments, see our post on Trusted Research Environments.
Technical Safeguards for Your Analytics
The HIPAA Security Rule mandates specific technical controls for electronic PHI (ePHI), which are the backbone of HIPAA-compliant data analytics. These are not optional; they are required specifications for protecting data.
- Access Controls: This is the cornerstone of data security, ensuring that users can only access the minimum necessary information to perform their job functions (the Principle of Least Privilege). Implementation requires unique user IDs for every person, role-based access control (RBAC) policies that define permissions for different job categories, and procedures for emergency access. It also includes automatic logoff features to prevent unauthorized access to unattended workstations.
- Encryption and Integrity: Data must be protected both when it is being transmitted over a network and when it is stored. Encryption in transit is typically achieved using protocols like SSL/TLS to secure data moving between a user and a server. Encryption at rest involves encrypting data stored on servers, databases, and endpoint devices using strong algorithms like AES-256. This renders the data unreadable and unusable in the event of a physical theft or system breach. Integrity controls, such as checksums or digital signatures, are also required to ensure that ePHI is not improperly altered or destroyed.
- Audit Logs: Organizations must maintain detailed records of all activity involving ePHI. These audit logs create a forensic trail, tracking who accessed what data, when they accessed it, and what actions they performed (e.g., view, create, modify, delete). These logs are essential for detecting and investigating potential security incidents, monitoring for suspicious activity, and proving compliance to regulators during an audit.
- Authentication: This safeguard requires organizations to implement procedures to verify that a person or entity seeking access to ePHI is the one claimed. This typically involves passwords, but increasingly relies on stronger methods like multi-factor authentication (MFA), which combines something the user knows (password) with something they have (a phone app or token).
For a deeper dive, see our guide on Key Features of a Trusted Research Environments.
Administrative and Physical Safeguards
Beyond technology, HIPAA requires administrative and physical safeguards to create a comprehensive security program.
- Security Officer Role: Every covered entity and business associate must designate a specific individual as their Security Officer. This person is responsible for the overall development and enforcement of all security policies and procedures, conducting regular risk assessments, managing security training for the workforce, and leading the incident response effort.
- Contingency Plans: Organizations must be prepared for emergencies. This requires having robust data backup plans, disaster recovery plans, and an emergency mode operation plan. The goal is to ensure that critical patient data can be recovered and that healthcare operations can continue with minimal disruption in the event of a natural disaster, cyberattack, or system failure.
- Facility Access Controls: These are policies designed to limit physical access to buildings and specific areas where ePHI is stored, such as data centers or server rooms. Measures include implementing visitor sign-in logs and escort policies, using security systems, and ensuring doors to sensitive areas are locked and monitored.
- Workstation Security: This involves creating and enforcing rules that govern the use and security of all workstations that access ePHI, including both on-site desktops and remote laptops. Policies should cover proper use, screen-locking protocols, and the secure disposal of devices and media that contain ePHI (e.g., through degaussing or physical destruction).
Frequently Asked Questions about HIPAA-Compliant Data Analytics
Navigating HIPAA-compliant data analytics often brings up common questions. Here are concise answers to the most frequent ones.
Is Google Analytics HIPAA compliant?
No, standard Google Analytics is not HIPAA-compliant. The primary reason is that Google does not offer a Business Associate Agreement (BAA) for the service. Without a BAA, a HIPAA-covered entity cannot use it on any digital property where PHI might be collected or transmitted. Configuring the tool to minimize PHI collection does not resolve the fundamental compliance gap left by the absence of a BAA. Google’s own documentation advises against using the service in ways that would create HIPAA obligations. See Google’s statement on HIPAA.
What is the difference between PHI and PII?
Think of PHI as a specialized, legally protected subset of PII. Personally Identifiable Information (PII) is any data that can identify an individual. Protected Health Information (PHI) is PII that is related to health, created or received by a HIPAA-covered entity, and protected under federal law. For example, your name on a magazine subscription is PII. Your name on a hospital bill is PHI. Because PHI has much stricter handling requirements, general-purpose analytics tools are often unsuitable for healthcare.
How can I ensure my entire data stack is compliant?
Ensuring your entire stack is HIPAA-compliant requires a holistic approach, as you are only as strong as your weakest link. Key steps include:
- End-to-end governance: Implement clear policies for data collection, access, retention, and security across all systems.
- Audit all data sources: Ensure every system feeding into your analytics (EHRs, patient portals, CRMs) is compliant.
- Vet all integrations: Scrutinize every API, connector, and data pipeline for security vulnerabilities.
- Secure BAAs with all partners: Obtain a signed BAA from every vendor that may handle PHI on your behalf.
This is why many organizations choose integrated platforms designed specifically for healthcare, where compliance is built-in rather than bolted on.
Conclusion: Enabling Secure, Data-Driven Healthcare

The future of healthcare is data-driven, but it must be built on a foundation of security and trust. HIPAA-compliant data analytics is not just a regulatory hurdle; it’s the cornerstone of responsible innovation in medicine.
Getting compliance right allows us to accelerate drug findy, improve patient outcomes, and advance medical research—all while protecting individual privacy. The key is to choose the right strategy, whether self-hosting, partnering with trusted vendors, or leveraging specialized data governance platforms. The common thread is an unwavering commitment to patient privacy.
At Lifebit, our platform is built on this principle. Our federated AI platform enables secure, real-time access to global biomedical data while maintaining the highest standards of privacy and compliance. Through our Trusted Research Environment (TRE), Trusted Data Lakehouse (TDL), and R.E.A.L. (Real-time Evidence & Analytics Layer), we deliver the insights that drive medical breakthroughs, ensuring every byte of data remains protected.
We believe that innovation and compliance are not mutually exclusive. By achieving both, we can build a healthcare system that is both more intelligent and more trustworthy. The journey requires vigilance, but with the right platform and partners, the future of data-driven healthcare is bright.

