The Ultimate Guide to Lifebit’s Trusted Research Environment

Introduction: The Ticking Clock on Secure Health Data Research
Lifebit’s Trusted Research Environment is a federated, cloud-based platform enabling researchers to securely analyze sensitive health data where it resides—without moving it—while maintaining compliance with global regulations like GDPR and HIPAA.
Key Features:
- Federated Architecture: Analysis happens where data lives, eliminating risky data transfers.
- Security-by-Design: Zero-trust model, end-to-end encryption, and role-based access control.
- 5x Faster: Rapid cohort creation (30 seconds) and 1-click analysis deployment (GWAS, VEP, PRS).
- Compliance-Ready: Meets GDPR, HIPAA, ISO 27001, SOC 2, and FedRAMP standards.
- Proven Scale: Handles datasets from 250M+ patients globally.
- Airlock™ System: Pioneering export control for secure data egress.
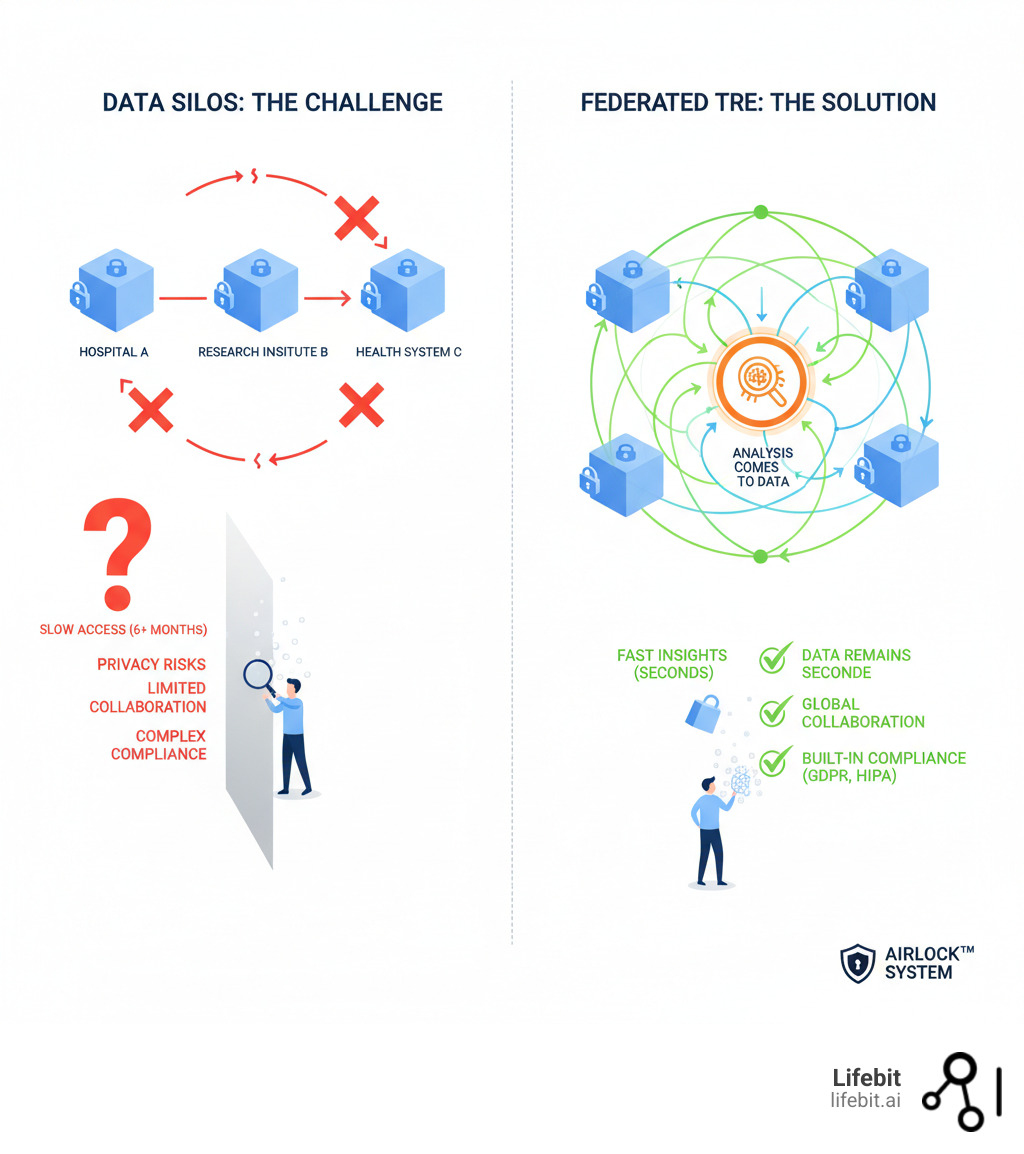
The world of biomedical research is drowning in data but struggling to access it safely. Biobanks manage petabytes of information, yet research access can take six months or longer—if it happens at all. The problem is risk.
Traditional methods require copying and moving sensitive patient data, increasing breach potential, threatening privacy, and costing lives through delays. Data silos, privacy regulations, and security concerns prevent collaboration, leaving researchers unable to access vital insights.
This is the paradox of modern precision medicine: more data than ever, but we can’t use it effectively without compromising patient safety.
While Trusted Research Environments (TREs) emerged as a solution, most still rely on centralized models that require data movement, creating bottlenecks, duplicating costs, and introducing new risks.
Lifebit’s Trusted Research Environment takes a different approach: federated by design.
Instead of moving data to researchers, it brings analysis to the data. Instead of copying datasets, it connects them. It delivers both speed and security. This fundamental shift enables global collaboration while keeping sensitive health information exactly where it belongs.
I’m Maria Chatzou Dunford, CEO and Co-founder of Lifebit. With a PhD in Biomedicine and over 15 years in the field, I created Lifebit’s Trusted Research Environment to solve the exact challenges I faced as a researcher: knowing the data existed but being unable to access it safely or quickly enough to make a difference.
Lifebit’s Trusted Research Environment glossary:
- What is a Trusted Research Environment?
- What is a Secure Data Environment (SDE)
- secure research environment
The Federated Revolution: Why Bringing Analysis to Data is a Game-Changer
For decades, health data research meant copying data to a central location. This model seemed logical but created immense risk. Every time you move sensitive health data, you create another potential breach point, require new approvals, and steer a maze of data sovereignty laws that can grind research to a halt.
Traditional Trusted Research Environments (TREs) improved security by creating central repositories, but they still relied on moving data, relinquishing control, and creating bottlenecks.
Lifebit’s Trusted Research Environment flips this model. Instead of moving data to analysis, we bring analysis to data. Your sensitive health information stays in your secure infrastructure, under your control. If the data never moves, it can’t be intercepted. If it’s never duplicated, there are fewer copies to protect. If it stays in its original jurisdiction, data sovereignty laws are no longer a barrier.
The table below shows just how profound these differences are:
| Feature | Traditional Centralized TREs | Lifebit’s Federated TREs |
|---|---|---|
| Data Movement | Data is copied and moved to a central repository. | Analysis comes to data; data stays in its original location. |
| Security Risk | Higher risk due to data movement and duplication. | Lower risk; no data movement, reduced re-identification risk. |
| Data Control | Data owner relinquishes some control to the central TRE. | Data owner retains full control within their own infrastructure. |
| Compliance | Challenges with data residency across jurisdictions. | Simplifies compliance with data residency laws. |
| Cost Model | Duplication costs, data transfer fees. | Optimized costs by avoiding data duplication and transfers. |
| Scalability | Limited by central TRE’s infrastructure. | Highly scalable, leveraging distributed infrastructures. |
| Collaboration | Requires data consolidation before collaboration. | Enables secure collaboration across distributed datasets. |
| Speed | Delays due to data ingestion and harmonization. | 5x Faster for cohort creation and analysis. |
How a Federated TRE Works
The core principle is simple: data never leaves home. With Lifebit’s Trusted Research Environment, patient-level data stays in its original secure environment. Always. Our platform acts as an orchestrator, connecting researchers to data through a multi-step, security-first process.
1. Federated Data Discovery through Metadata Catalogs:
The process begins not with data, but with data about the data. We work with data custodians to create a centralized, searchable catalog of metadata. This catalog contains no patient-level information. Instead, it holds descriptive, non-sensitive variables like the availability of genomic data, clinical diagnoses (using standardized codes like ICD-10), age ranges, and specimen types. Researchers can query this federated catalog to discover and build cohorts across multiple, distributed datasets. For example, a researcher could ask, “How many female participants, aged 50-65, with a diagnosis of type 2 diabetes and available whole-genome sequencing data, exist across Biobank A in the UK and Biobank B in Germany?” The system returns only an aggregate count, allowing the researcher to assess the feasibility of a study without ever accessing the underlying sensitive data.
2. In-Situ Analysis with Containerized Tools:
Once a cohort is identified and approved for a project, in-situ analysis begins. Instead of pulling data out, the platform pushes the analysis in. This is achieved using containerization technologies like Docker and Singularity. Researchers package their analytical pipelines, scripts, and software dependencies into a secure, self-contained “container.” This container is then deployed directly into the data owner’s private cloud or on-premise infrastructure. The analysis runs inside this isolated environment, querying the data where it sits. This model inherently enforces data residency and sovereignty rules, as the raw data never crosses jurisdictional borders.
3. Secure Results Egress:
After the analysis is complete, only the aggregated, non-identifiable results are eligible for export, and even then, only after passing through our stringent Airlock™ system for review and approval. This ensures that no sensitive information ever leaves the secure perimeter.
Key Benefits of the Federated Approach
The federated model open ups new possibilities for precision medicine:
- Inherent Security: Because data never moves, the primary attack vector disappears. Our security-by-design approach aligns with top global standards (GDPR, HIPAA, ISO 27001, SOC 2) by making protection part of the architecture.
- Complete Data Control: Your organization retains full ownership and governance over your data within your own infrastructure. You decide who gets access and when.
- Dramatic Cost Reduction: Centralized models incur staggering and often hidden costs. These include cloud egress fees for moving petabytes of data, the expense of creating and maintaining redundant storage infrastructure, and the operational overhead of managing complex data transfer agreements. The federated approach eliminates these expenditures. By bringing computation to the data, you avoid data transfer fees entirely. You also eliminate the need for a costly central data lake, as the data remains in its original, optimized storage environment. This shifts investment from data logistics to data science, maximizing the value of research budgets.
- Seamless Global Collaboration: The federated model dismantles the geographical and legal barriers that have historically crippled international research. Consider a study on a rare pediatric cancer. No single institution has enough patient data for a statistically significant analysis. With Lifebit’s federated TRE, a consortium of hospitals in the US, UK, and Japan can collaborate. Each hospital’s data remains within its own secure environment, fully compliant with its respective regulations (HIPAA, GDPR, APPI). The analysis tools are sent to each location, the computations are performed locally, and the anonymized results are aggregated to produce powerful insights that would be impossible to achieve otherwise. This enables true global science without compromising patient privacy or national data laws.
- Increased Speed: Lifebit’s Trusted Research Environment is 5x faster than traditional methods. Cohorts can be assembled in 30 seconds, and analyses can launch with a single click.
- Guaranteed Results: We are so confident in our platform that we contractually guarantee results. This approach is battle-tested at scale, handling data from over 250 million patients globally.
The federated revolution is here, changing what’s possible when security, speed, and collaboration work together.
The Security Architecture of Lifebit’s Trusted Research Environment
For sensitive patient data, security must be the foundation. At Lifebit, our federated platform is built with security-by-design as a core principle, meaning every architectural decision is made with protection in mind. Our multi-layered defense system is crafted to protect participant data while enabling transformative research.
Our approach begins with a zero-trust security model: no user or system is automatically trusted. Every access request is verified, every action authenticated, and every movement monitored. This commitment aligns with frameworks like the Scottish government’s A charter for safe havens, setting the standard for handling sensitive patient records.

Technical safeguards in Lifebit’s Trusted Research Environment include:
- Network segmentation to isolate components and prevent lateral movement.
- Double encryption for data at rest and in transit, with regular key rotation.
- Continuous monitoring and auditing with complete audit trails to detect threats in real-time.
Our security is verified by independent third parties, meeting stringent certifications including ISO 27001, SOC 2 Type II, and HITRUST CSF.
The ‘Five Safes’ Framework as a Core Principle
We embed the internationally recognized ‘Five Safes’ framework into every process to provide a holistic governance structure that balances data utility with ironclad security. You can learn more about it here: The 5 Safes Framework explained. Our platform operationalizes this framework through integrated technical and administrative controls.
-
Safe People: We ensure that only authorized individuals can access the data. This is more than a simple login. Every researcher is vetted through a multi-step process that includes verification of their institutional affiliation, confirmation of required training (e.g., in information governance), and approval by a formal Data Access Committee (DAC). Access is granted on a “least privilege” basis, meaning researchers are only given permissions for the specific data and tools necessary for their approved project.
-
Safe Projects: We guarantee that data is used for ethical and scientifically valid purposes. Before any project begins, it must undergo a rigorous review by an Institutional Review Board (IRB) or an equivalent ethics committee. The review assesses the project’s scientific merit, its potential for public benefit, and its data minimization plan, ensuring the proposed research is appropriate and in the public interest.
-
Safe Settings: We provide a secure, locked-down computational environment to prevent unauthorized data disclosure. The analysis workspace is completely isolated from the public internet. Technical controls are enforced to disable copy-paste, screen-sharing, and downloads. All software and analytical tools brought into the environment are scanned for vulnerabilities and approved before use, preventing the execution of malicious or unverified code.
-
Safe Data: We minimize the risk of re-identification by controlling the form of the data researchers can access. For most discovery and cohort-building activities, researchers only interact with aggregated metadata. For analysis, data is typically provided in a de-identified or pseudonymized state. The level of data granularity is determined by the data controller based on the risk profile of the project, ensuring proportionality.
-
Safe Outputs: We prevent the leakage of sensitive information by meticulously checking all results before they can be exported. Our Airlock™ system (detailed below) acts as a final checkpoint. Researchers cannot directly export files. Instead, they must submit an export request, where a designated data steward or reviewer scrutinizes the output for any potentially disclosive information, such as small cell counts (e.g., results pertaining to fewer than 10 individuals) or individual-level data plots. Only results that are confirmed to be aggregated and non-identifiable are approved for release.
Ensuring Regulatory Compliance and Data Privacy
Lifebit’s Trusted Research Environment adheres to the highest global security regulations, including GDPR, HIPAA, ISO 27001, SOC 2, and FedRAMP standards.
Critical technical controls are built directly into the platform. End-to-end encryption protects data throughout its lifecycle, while role-based access control (RBAC) ensures researchers only see data authorized for their specific project. Full audit trails provide complete transparency and accountability.
Our most innovative feature for enforcing the ‘Safe Outputs’ principle is the Airlock™ system. This technology functions as a digital air gap, creating a robust barrier between the secure analysis environment and the outside world. By default, all data exports are blocked.
The workflow is designed for maximum security and accountability:
- Request Submission: A researcher completes their analysis and wishes to export a results file (e.g., a summary statistics table, a graph, or a report). They submit the file through the Airlock™ portal, along with a justification for the export.
- Automated Checks: The system can perform initial automated checks for common disclosive patterns, flagging potential issues for the human reviewer.
- Manual Review: The request triggers a notification to the designated data controller or their appointed information governance team. This reviewer accesses a secure, isolated viewer to inspect the requested output file. They cannot edit the file, only view it.
- Approve or Deny: The reviewer assesses the file against pre-defined disclosure control rules. They check for small cell counts, direct identifiers, or any combination of attributes that could potentially re-identify an individual. Based on this assessment, they either approve or deny the request.
- Secure Release: If approved, the file is securely released to the researcher’s designated external location. If denied, the researcher receives feedback on why the request was rejected and what changes are needed for approval.
This pioneering, human-in-the-loop process provides data owners with absolute control over data egress, ensuring that only safe, aggregated, and anonymized insights leave the TRE. It is a cornerstone of building and maintaining participant trust.
Security isn’t about creating barriers; it’s about building the right protections so groundbreaking research can happen safely, ethically, and at scale.
From Cohorts to Findies: Features and Real-World Impact
Lifebit’s Trusted Research Environment isn’t just about locking down data—it’s about open uping insights. We built our platform so security and speed work together, eliminating the frustration of complex interfaces and endless waiting. Our user-friendly tools let you focus on the science.

Built for scalability and adhering to FAIR data principles (Findable, Accessible, Interoperable, Reusable), our platform ensures your research produces results that others can build on.
Key Features of Lifebit’s Trusted Research Environment
Purpose-built for precision medicine, our TRE simplifies the complexity of multi-modal and multi-omic data.
-
Rapid Cohort Creation: The ability to build precise cohorts in as little as 30 seconds is a direct result of our federated architecture. Instead of running slow, computationally expensive queries against raw, petabyte-scale datasets, researchers interact with a highly optimized and pre-indexed metadata catalog. This allows for near-instantaneous exploration of the data landscape to determine study feasibility and define patient groups based on complex criteria, transforming a process that traditionally takes months into one that takes minutes.
-
1-Click Analysis Deployment: We eliminate the significant technical overhead of setting up complex bioinformatics analyses. For common, standardized workflows like Genome-Wide Association Studies (GWAS), Variant Effect Predictor (VEP), and Polygenic Risk Scores (PRS), we offer pre-configured, push-button deployments. This allows researchers to launch a population-scale analysis with a single click, democratizing access to powerful genomic tools.
-
Flexible Pipeline Integration: We recognize that research requires flexibility. Our platform allows you to “bring your own tools” securely. Using our 3-click deployment system, researchers can easily import their existing containerized pipelines built with popular workflow managers like Nextflow, Cromwell-WDL, and Snakemake. The platform handles the orchestration, ensuring the pipeline runs efficiently and securely within the TRE, whether it’s a simple script or a multi-stage GATK variant calling workflow.
-
Interactive Tools for Exploratory Science: Beyond batch-processing pipelines, modern research requires interactive data exploration. We have natively integrated familiar, powerful tools like JupyterLab and RStudio directly into the secure environment. This allows data scientists to perform exploratory analysis, develop novel algorithms, and visualize data in real-time, all while benefiting from the full security, compliance, and governance controls of the federated TRE.
Practical Applications and Use Cases
Our TRE powers research across public health, federal agencies, pharma, and biotech.
-
Genomics Research: Process Next-Generation Sequencing (NGS) data at scale for population genomics, rare disease studies, and target identification.
-
AI and Machine Learning: Our platform is built for the next generation of medical AI. We enable federated learning, a revolutionary approach to training machine learning models. Instead of pooling all data in one place (a major privacy risk), the central model is sent to each participating institution’s local data. The model is trained on the local data, and only the resulting mathematical updates (gradients or weights), not the data itself, are sent back to be aggregated. This process is repeated, iteratively improving the global model with insights from all datasets without any of them ever being moved or exposed. This allows for the creation of more accurate, robust, and generalizable AI models for tasks like medical image analysis or disease prediction.
-
Real-World Evidence (RWE): Generating RWE for regulatory submissions requires an unbreakable chain of evidence. Our Trusted Data Lakehouse™ is specifically designed for this. It provides immutable data lineage and provenance, meaning it automatically captures a complete, auditable record of every action performed on the data. This includes who accessed the data, what analysis was run, which version of the software was used, and how the data was transformed. This end-to-end traceability is critical for meeting the stringent validation requirements of regulatory bodies like the FDA and EMA, enabling the use of real-world data to support drug approvals and post-market surveillance.
-
Pharmacovigilance: Enable real-time insights into drug safety and efficacy to monitor medications and detect safety signals early.
Case Study: Powering Population Health with CanPath
Our partnership with the Canadian Partnership for Tomorrow’s Health (CanPath), Canada’s largest population health study with over 330,000 participants, demonstrates our platform’s real-world impact. The goal of CanPath is to understand the complex interplay of genetics, environment, lifestyle, and behavior in causing chronic diseases. The dataset is incredibly rich and diverse, containing everything from detailed health and lifestyle questionnaires to physical measurements, biological samples (blood, urine), clinical data, and increasingly, multi-omic data like whole-genome sequencing (WGS).
Hosted on AWS infrastructure and supported by Genome Canada’s GAPP, the CanPath TRE, powered by Lifebit, provides a single, secure gateway for approved researchers to access this invaluable national resource. Previously, accessing this data was a complex, time-consuming process. Now, researchers can log into the platform and immediately begin exploring the data and running analyses.
They can investigate critical public health questions, such as identifying genetic risk factors for cancer, studying the impact of air pollution on respiratory health across different provinces, or analyzing how diet influences the risk of cardiovascular disease. Researchers can bring their own containerized tools or use pre-loaded ones to perform large-scale GWAS, build polygenic risk score models, and train machine learning algorithms on imaging data, all without needing massive local computing power or moving any sensitive participant data. This mirrors the success of other world-leading initiatives like Genomics England collaborative research, democratizing access and accelerating discoveries that will improve the health of Canadians for generations to come.
Frequently Asked Questions about Federated TREs
Understanding how federated TREs work is crucial for researchers and data custodians. Here are answers to the most common questions.
What is the difference between a standard TRE and a Federated TRE?
A standard TRE is a central vault: all data must be copied and moved to it, which is risky, expensive, and creates compliance issues.
A Federated TRE, like Lifebit’s Trusted Research Environment, flips this model. It brings the analysis to the data, which never leaves its original, secure location. This eliminates risky data transfers, simplifies compliance with data sovereignty laws, and gives data owners complete control while reducing costs.
How is data security and patient privacy guaranteed?
We guarantee security through a multi-layered defense:
- Federated Architecture: Patient-level data never moves, eliminating the primary risk of interception.
- ‘Five Safes’ Framework: We ensure Safe People, Projects, Settings, Data, and Outputs.
- Technical Safeguards: We use end-to-end encryption, role-based access controls (RBAC), and full audit trails.
- Airlock™ System: Our pioneering export control system ensures only aggregated, anonymized results leave the TRE after a strict review process.
- Compliance: Our platform is fully compliant with global standards like GDPR, HIPAA, ISO 27001, SOC 2, and FedRAMP.
What are the costs associated with using a TRE like the CanPath platform?
For the CanPath TRE, there is no fee for platform access. The only cost is for the cloud computing resources (AWS infrastructure) you use during analysis.
Researchers purchase computing credits and can buy more as needed. The Principal Investigator (PI) can view usage and set cost limits. The system sends automatic notifications at 80% and 90% of credit usage to help manage budgets.
You can estimate expenses using tools like the AWS Pricing Calculator. For help optimizing costs, you can book an appointment with a Lifebit Solutions Specialist. You only pay for the computing power you use, with full visibility and control over spending.
The Future is Federated: Accelerate Your Research Today
The future of precision medicine is here, and it’s federated. Traditional, centralized models for handling sensitive health data are too slow, risky, and complex for modern research.
Lifebit’s Trusted Research Environment is a fundamental reimagining of research that prioritizes speed without sacrificing security, and enables collaboration without compromising control. By bringing analysis to data, we’ve solved problems that once seemed impossible.
This means no more six-month waits for data access, no more choosing between insights and privacy, and no more missed opportunities. With our federated approach, you can create cohorts in 30 seconds, deploy analyses in 1-click, and collaborate globally—all while data stays securely in place.
We envision a future of seamless federated learning, where institutions worldwide train powerful AI models together without exposing sensitive data. We are pioneering solutions like differential privacy and homomorphic encryption to make this a reality.
Our commitment is to solve the hardest problems in precision medicine. With a track record of managing data from over 250M+ patients and partnerships with leaders like CanPath and Genomics England, Lifebit is leading this change.
The obstacles of siloed data, compliance delays, and security fears no longer need to stand in your way. Lifebit’s Trusted Research Environment provides the tools to move forward with confidence. The findies that will save lives tomorrow depend on the research you start today.

