Everything You Need to Know About a Secure Data Environment (SDE)
Why Secure Data Environments Are Revolutionizing Healthcare Research
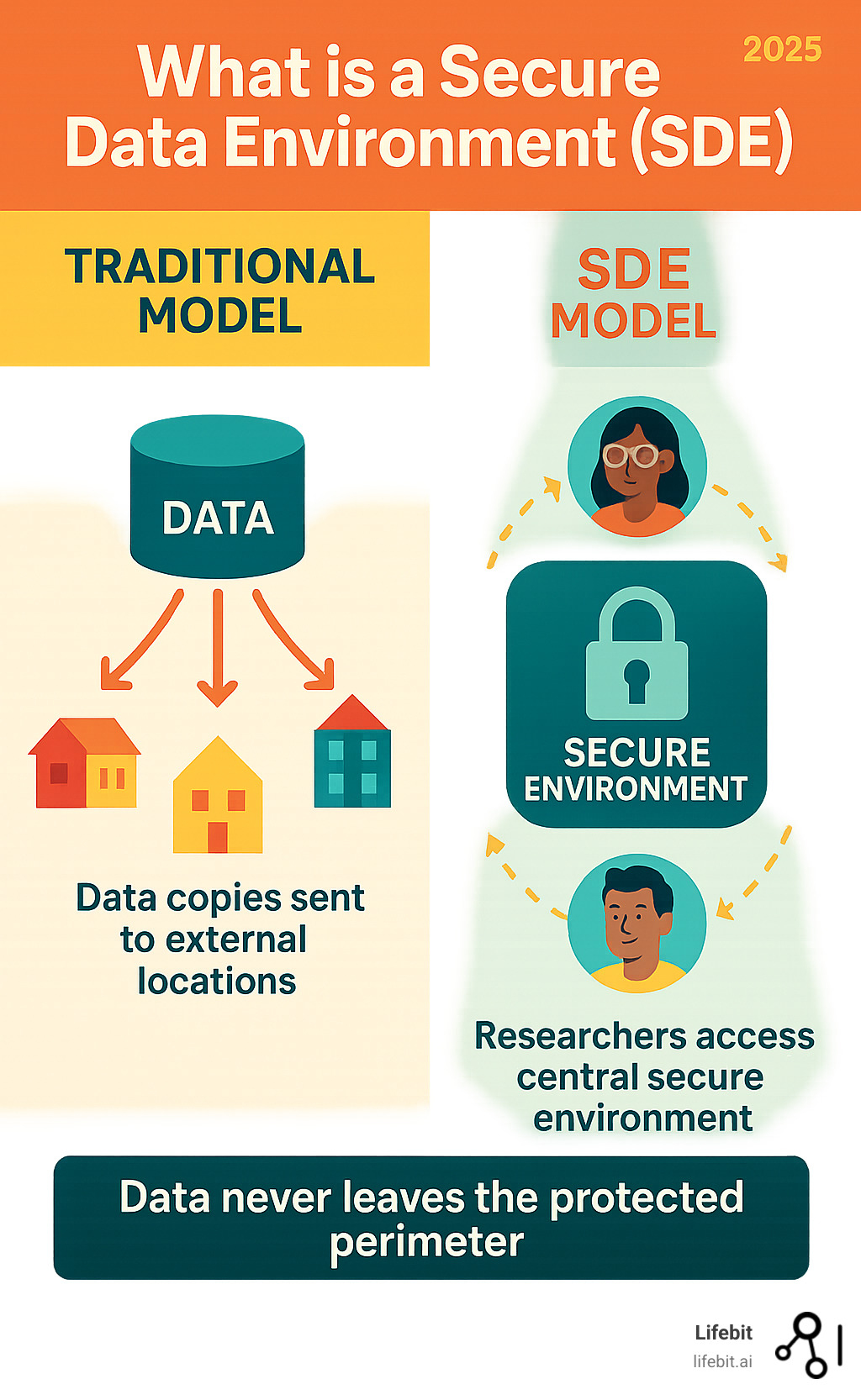
What is a Secure Data Environment (SDE)? It’s a secure platform allowing approved researchers to analyze sensitive health data without it ever leaving the controlled environment. This approach balances the potential of health data with the need to protect patient privacy.
Key Features of SDEs:
- Secure by design: Data remains within protected boundaries.
- Controlled access: Only vetted researchers with approved projects can enter.
- No data downloads: Analysis happens inside the environment; raw data never leaves.
- Built-in safeguards: Encryption, audit trails, and output checking protect privacy.
- Real-time collaboration: Multiple researchers can work together securely.
For decades, research relied on sending copies of sensitive datasets to researchers, a risky approach that created vulnerabilities. SDEs represent a paradigm shift: instead of sharing data, we bring researchers to the data in secure, controlled environments.
This change is driven by initiatives like the NHS “Data Saves Lives” strategy, which is establishing a network of SDEs across England. The results are clear: platforms like UK Biobank have enabled over 10,000 research publications by providing secure access to data from 500,000 participants.
I’m Maria Chatzou Dunford, CEO and Co-founder of Lifebit. With over 15 years of experience developing secure, federated platforms for genomics and biomedical research, I’ve seen how SDEs are accelerating the speed and safety of medical findy.
What is a Secure Data Environment (SDE) terms to know:
What is a Secure Data Environment (SDE) and Why is it a Game-Changer?
Think of a Secure Data Environment (SDE) as a digital research lab where scientists work with sensitive health information that can never leave. It’s a specialized platform for handling health and social care data with top-tier security. Approved researchers enter this controlled environment to perform analysis, but the raw data cannot be downloaded, copied, or screenshotted. This solves a major challenge: open uping the life-saving potential of health data while virtually eliminating the risk of data breaches.

The Problem with Traditional Data Sharing
For decades, the standard research model involved data custodians sending physical or digital copies of datasets to researchers around the world. This “data sharing” approach was fraught with risk and inefficiency. Every copy created a new point of vulnerability, increasing the chances of a data breach through loss, theft, or cyberattack. Data custodians lost control and oversight the moment the data left their servers, making it impossible to enforce usage agreements or track how the data was being analyzed. Furthermore, this process was slow and cumbersome, often involving lengthy legal agreements and insecure transfer methods for each individual request, delaying critical research by months.
The Core Principle: From Data Sharing to Secure Data Access
The SDE model flips this outdated approach on its head. Instead of sending data out, we bring authenticated researchers to the data within a secure digital perimeter. Researchers are given access to a virtual workspace where they can use analytical tools to query and model the data, but they cannot move the raw data itself. This is often described as “bringing the code to the data.” This fundamental shift gives data custodians complete control and visibility over their assets, dramatically improving security, accountability, and the speed of research.
Key Characteristics of a Secure Data Environment
SDEs are built on multiple layers of protection to ensure they are trustworthy. They are secure by design, with security integrated into every aspect of the platform. Key characteristics include:
- Strict Access Controls: Access is never open. It is granted on a per-project basis to specific, named researchers whose identities have been verified (often using multi-factor authentication). Role-Based Access Control (RBAC) ensures that users can only see the data and use the tools that are strictly necessary for their approved project, adhering to the principle of least privilege.
- Comprehensive Monitoring and Auditing: Every action taken within the SDE is logged and monitored in real-time. This includes user logins, data queries, analysis scripts run, and attempts to export results. This detailed audit trail provides full accountability and allows security teams to detect and respond to any anomalous or unauthorized activity.
- De-identified Data: Before being made available for research, data undergoes a process of de-identification. At a minimum, this involves pseudonymisation, where direct identifiers like names and addresses are replaced with a non-identifying code. This minimizes the risk of re-identification while preserving the data’s scientific value, as records for the same individual can still be linked over time.
- Contained Analysis and Secure Outputs: All computation and analysis happens within the SDE’s secure boundary. Researchers cannot download, copy, print, or even screenshot the raw data. When their analysis is complete, they can request to export their results (e.g., statistical tables, graphs, trained models). These results must pass through a stringent output checking process, often called a digital “airlock,” where they are reviewed by trained staff to ensure they are aggregated and contain no potentially disclosive information before being released.
These features create a robust framework for sensitive data research. For more on this, explore Preserving Patient Data Privacy and Security.
The Driving Force: The NHS “Data Saves Lives” Strategy
The UK’s National Health Service is a global pioneer in the transition to SDEs. This shift was heavily influenced by Professor Ben Goldacre’s 2022 review, “Better, Broader, Safer,” which highlighted the inefficiencies and risks of the old data sharing model. The review called for the universal adoption of a small number of accredited SDE platforms to replace the “Wild West” of thousands of bespoke data-sharing arrangements. In response, the UK government launched The “Data Saves Lives” initiative. This ambitious programme, backed by £175 million in funding, aims to make SDEs the default and, eventually, the only way to access NHS data for research. The policy shift delivers improved patient privacy, security, and research efficiency. By enabling faster access to linked datasets, SDEs accelerate the findy of new treatments. Crucially, this initiative aims to build public trust by demonstrating that sensitive information can be used for groundbreaking research while remaining secure.
How SDEs Guarantee Unprecedented Data Privacy and Security
Trust in a Secure Data Environment (SDE) comes from its multiple layers of protection. SDEs combine robust governance, advanced technical safeguards, and strict procedural controls to build public confidence in the use of sensitive health data for research. This comprehensive approach, often encapsulated by the Five Safes Framework, is vital when handling personal medical and genetic information. For more on this, see our guide on Data Security in Nonprofit Health Research.

The Five Safes Framework: A Blueprint for Trust
At the core of SDE governance is the internationally recognized Five Safes Framework, the gold standard for managing sensitive data access. It provides a holistic security model by ensuring that five key dimensions are robustly managed:
- Safe People: This principle ensures that only trustworthy and appropriately trained researchers can access data. Individuals must undergo a vetting process, which may include identity verification, background checks, and mandatory training on information governance, data security, and statistical disclosure control. They must be affiliated with a recognized institution and become accredited users, legally bound to uphold the rules of the SDE.
- Safe Projects: This ensures that data is only used for legitimate, ethical, and valuable research that serves the public good. Every research proposal is scrutinized by an independent review committee, such as a Data Access Committee (DAC), which includes scientific experts, ethicists, and public representatives. The committee assesses the project’s scientific merit, its ethical implications, and its potential to deliver tangible benefits to health and social care. Commercial or marketing uses are strictly forbidden.
- Safe Settings: This refers to the security of the environment itself. The SDE must be a technological fortress, employing state-of-the-art cybersecurity measures to prevent unauthorized access or data leakage. This includes robust network security, intrusion detection systems, regular penetration testing, and secure software development practices. The environment must be resilient and capable of withstanding sophisticated cyber threats.
- Safe Data: This principle focuses on minimizing the risk of re-identification within the dataset. Data custodians apply various disclosure control techniques before making data available. This always includes removing direct identifiers (like names and addresses) and often involves pseudonymisation. In some cases, more advanced techniques may be used, such as data reduction (removing certain variables) or perturbation (adding statistical noise), to further protect privacy without destroying the data’s utility.
- Safe Outputs: This is the final checkpoint, ensuring no sensitive information leaves the secure environment with the research results. All outputs, whether they are tables, charts, or statistical models, are carefully checked before they can be exported. This “airlock” process is designed to prevent the release of any data that could, either directly or indirectly, be used to identify an individual. For example, checkers will look for small cell counts (e.g., a table showing only one person in a specific category) that could be disclosive.
This framework creates the transparency and accountability needed to build public trust. You can learn more at The Five Safes framework explained.
Technical and Procedural Safeguards
Practical security measures bring the SDE concept to life. These safeguards create a “defense in depth” strategy where multiple independent layers of security work together:
- Data Encryption: All data within an SDE is encrypted, both when it is stored (“at rest”) and when it is being transmitted (“in transit”). This means that even if an attacker were to gain access to the physical servers or intercept network traffic, the data would be unreadable without the cryptographic keys.
- Strict Access Controls and Multi-Factor Authentication (MFA): User access is tightly controlled. MFA is standard, requiring users to provide at least two forms of verification (e.g., a password and a code from their phone) to prove their identity before they can log in. This prevents unauthorized access even if a password is stolen.
- Detailed Audit Trails and Continuous Monitoring: The SDE logs every single action performed by every user. This creates an immutable record that can be used to investigate any security incidents and hold users accountable. Automated monitoring systems continuously scan these logs for suspicious activity, alerting security teams to potential threats in real-time.
- Prohibition of Data Downloads: This is the foundational principle of an SDE. Technical controls are in place to make it impossible for a user to download, copy-paste, or screenshot the raw data. All analysis is performed on a remote virtual machine, and the user only interacts with a view of the data, not the data itself.
- Output Checking and Statistical Disclosure Control: The “airlock” services that check all outputs are a critical procedural safeguard. This is typically a manual or semi-automated process carried out by trained disclosure experts who scrutinize results to ensure they meet strict statistical criteria for non-disclosure before approving their release.
AI Enabled Data Governance can further automate and strengthen these safeguards.
Gaining Access: The Process for Approved Researchers
Access to an SDE is a rigorous, multi-stage process designed to uphold the Five Safes. A typical workflow includes:
- Application Submission: The researcher submits a detailed application through a centralized portal, such as the NHS Data Access Request Service (DARS). The application must clearly define the research questions, the specific data required (adhering to the principle of data minimisation), the methodology, and the expected public benefit.
- Review and Approval: The application is scrutinized by one or more independent committees. A scientific panel assesses its research merit, while an ethics or governance committee evaluates its compliance with legal and ethical standards. This stage can take several weeks or months to ensure thoroughness.
- Data Sharing Agreement (DSA): If the project is approved, a legally binding DSA is executed between the researcher’s institution and the data custodian. This contract outlines the terms of use, security responsibilities, and penalties for non-compliance.
- User Accreditation and Training: The individual researchers named on the project must complete mandatory training on data privacy and security. They must formally agree to the rules of the environment and may need to obtain specific accreditation.
- Provisioning of Access: Only after all previous steps are complete is the researcher’s account created and provisioned with access to the specific dataset and tools approved for their project within the SDE.
The Transformative Benefits of SDEs for Research and Healthcare
The shift to Secure Data Environment (SDE) models is about more than safety; it’s about open uping new possibilities for innovation, patient outcomes, and collaboration. By protecting data, SDEs liberate its potential while keeping privacy intact, making them truly transformative for healthcare research.

Accelerating Life-Saving Research and Findy
SDEs dramatically speed up the entire research lifecycle. By providing standardized, on-demand access to analysis-ready data, they cut down the time it takes to get a project started from months to days. This acceleration was powerfully demonstrated during the COVID-19 pandemic, where SDEs enabled researchers to rapidly analyze near-real-time data on infections, hospitalizations, and vaccine effectiveness, informing public health policy at a critical time.
The true power of SDEs lies in their ability to bring together diverse, large-scale datasets. By linking genomics, electronic health records (EHR), medical imaging, and even social determinants of health data, researchers can ask more complex questions and uncover previously hidden correlations. The UK Biobank, a landmark SDE, illustrates this perfectly. By providing secure access to deeply phenotyped data from 500,000 participants, it has enabled over 10,000 peer-reviewed publications, leading to findies in areas from cardiovascular disease to dementia. This faster access to linked datasets is the key to developing new diagnostics, personalizing treatments, and creating more effective public health strategies. For more on these benefits, see Advantages of Trusted Research Environments.
Enhancing Public Trust and Transparency
Public trust is the bedrock of health data research. Years of inconsistent data handling practices have led to public skepticism. Secure Data Environment (SDE) models are designed to rebuild that trust through radical transparency and robust security. By operating under clear governance structures and adhering to frameworks like the Five Safes, SDEs provide auditable proof that data is being used safely and ethically. This transparency is essential for creating a positive cycle: better security builds trust, which encourages public support for data use, enabling more life-saving research.
The Role of Patient and Public Involvement and Engagement (PPIE)
A critical component of building trust is meaningful Patient and Public Involvement and Engagement (PPIE). Modern SDEs are increasingly incorporating PPIE into their governance. This means that members of the public, including patients and their advocates, sit on the committees that review and approve research projects. They help ensure that the research is relevant to patient needs, that the consent process is clear, and that the public benefits are well-defined. This direct involvement gives the public a real voice in how their data is used, changing them from passive data subjects into active partners in the research enterprise. SDEs operate under strict ethical guidelines, such as the Data Ethics Framework, to ensure every project serves the public good.
Powering Advanced Analytics with AI and Federated Data Analysis
SDEs are not just secure storage containers; they are sophisticated computational powerhouses designed for modern data science. They provide access to the high-performance computing resources needed to train powerful AI and machine learning (AI/ML) models on vast, linked datasets. Researchers can use these platforms to develop AI algorithms that can detect cancer from medical images more accurately than the human eye or predict a patient’s risk of developing a chronic disease based on their EHR data.
The next frontier is Federated Data Analysis, a approach that allows algorithms to learn from multiple SDEs without the raw data ever moving or being pooled. In a federated network, an analysis query or machine learning model is sent to each participating SDE. The computation is performed locally within each secure environment, and only the aggregated, anonymous results or model updates are sent back to a central coordinator. This solves a major challenge in global health, enabling collaborative analysis across different hospitals, regions, and even countries, all while respecting local data privacy laws and governance rules (data residency). At Lifebit, our platform is built on this federated principle, enabling compliant, large-scale research that was previously impossible. For real-world examples, see our work on Clinical Trial Success with Secure Data Platforms.
SDEs in Action: Structure, Examples, and Challenges
In practice, several major Secure Data Environment (SDE) platforms are already demonstrating the power of this model, changing how researchers analyze health data at scale. While each has a unique focus and governance approach, they all share the core principle of bringing approved researchers to the data in a controlled setting. The UK has been a world leader in developing and deploying these platforms.
Profiles of Major UK SDEs
| SDE / Platform | Data Type | Access Model | Key Purpose |
|---|---|---|---|
| NHS England SDE | Administrative health data, hospital records, prescribing data | Centralized access through DARS approval | Population health research, service evaluation |
| UK Biobank | Genetic, lifestyle, imaging, and health data from 500,000 participants | Application-based access for approved research | Large-scale epidemiological and genetic studies |
| Genomics England | Genomic data from rare disease and cancer patients | Controlled access for approved genomic research | Precision medicine and rare disease research |
- NHS England SDE: This is the primary national SDE for accessing administrative health data from the NHS in England. It contains a wealth of information on hospital episodes, outpatient appointments, and prescribing data, making it an invaluable resource for population health research, evaluating the effectiveness of health services, and monitoring disease trends.
- UK Biobank: A globally renowned research resource, UK Biobank provides accredited researchers with access to de-identified genetic and health information from half a million UK participants. Its rich, longitudinal dataset, which includes everything from genomic sequences to lifestyle questionnaires and MRI scans, has been instrumental in thousands of studies on the causes, prevention, and treatment of a wide range of diseases.
- Genomics England: Established to deliver the 100,000 Genomes Project, this SDE holds whole-genome sequences linked with clinical data for NHS patients with rare diseases and their families, as well as patients with common cancers. It serves as a vital platform for research into precision medicine, helping to develop new diagnostics and targeted therapies based on a patient’s genetic makeup.
Case Study: The NHS Research Secure Data Environment Network
The most ambitious initiative in this space is the NHS Research Secure Data Environment Network. This is not a single platform but a coordinated, federated system of interconnected SDEs across England. Backed by £175 million in funding as part of the “Data Saves Lives” strategy, the network aims to provide faster, more standardized, and more secure access to NHS data by 2025. It includes a national SDE run by NHS England alongside a number of regional and domain-specific SDEs (e.g., focusing on cancer or cardiovascular data). The goal is to create an interoperable ecosystem where researchers, once approved, can analyze data across multiple SDEs seamlessly, under a common set of rules and technical standards. For more details, explore The NHS Research Secure Data Environment (SDE) Network.
Overcoming the Challenges and Limitations of SDEs
Despite their success, SDEs are a maturing technology and face several challenges that must be addressed:
- Interoperability and Standardization: A key goal of the NHS SDE Network is to solve this problem. Currently, different SDEs often have different data models, technical standards, and access policies. This makes it difficult for researchers to run the same analysis across multiple environments. Harmonizing these technical and governance aspects is a major undertaking.
- Cost and Sustainability: Building and maintaining a high-quality, secure SDE is expensive. The costs include cloud computing infrastructure, specialist software, and highly skilled staff (e.g., data engineers, security analysts, information governance experts). Developing sustainable funding models that balance affordability for academic researchers with the need to cover these significant operational costs is a critical challenge.
- Approval Bottlenecks: While rigorous vetting is essential for security and public trust, lengthy and complex approval processes can significantly slow down research. There is a constant tension between being thorough and being efficient. Efforts are underway to streamline and standardize the application and review process across the SDE network without compromising on safety.
- Scalability: As datasets grow larger (especially in genomics) and analytical methods become more complex (e.g., large AI models), SDEs must be able to scale their computational and storage resources on demand. Ensuring that the environment remains performant and responsive for a growing number of users and increasingly demanding workloads is a continuous technical challenge.
- The Skills Gap: Working within an SDE requires a different skillset than traditional research. Researchers need to be proficient in coding (e.g., in R or Python) and comfortable working in a remote, command-line-based environment. There is a recognized skills gap, and a need for more training and support to help the research community adapt to this new way of working.
The SDE community, including technology providers like Lifebit, is actively working to overcome these obstacles and build a more powerful and accessible research ecosystem.
Frequently Asked Questions about Secure Data Environments
As Secure Data Environment (SDE) technology represents a major shift in handling sensitive data, questions are common. Here are answers to the most frequent ones.
Are SDEs the same as Trusted Research Environments (TREs)?
Yes, the terms Secure Data Environment (SDE) and Trusted Research Environment (TRE) are essentially interchangeable. They both describe secure platforms for analyzing sensitive data without it ever leaving the controlled environment. The term SDE is often favored in UK government policy (particularly by the NHS), while TRE is common in academic and research communities. Other similar terms include “Data Clean Rooms” or “Secure Data Facilities.” Regardless of the name, the core principles of the Five Safes framework and bringing researchers to the data remain the same. For more on this, see What is a Trusted Research Environment?.
Who can access data in an SDE?
Access is strictly controlled and granted only to approved users for projects with a clear public benefit. This includes vetted researchers from academic institutions, charities, and the life sciences industry (such as pharmaceutical companies developing new medicines), as well as NHS analysts and local authority planners using data to improve health services. Every project is rigorously reviewed by an independent committee to ensure it is ethically sound and aims to improve health outcomes. Using data for purposes like marketing, setting insurance premiums, or any other non-health research purpose is strictly prohibited and enforced through legal agreements.
Can data be downloaded from an SDE?
No. This is a core security principle of a Secure Data Environment (SDE). Raw data can never be downloaded, copied, or screenshotted. Researchers work within a controlled virtual environment where the data resides. Technical controls prevent any movement of the raw data outside this perimeter. Only aggregated, non-identifiable results (like statistical summaries, graphs, or charts) can be exported. Even these outputs must pass through a stringent “airlock” checking process, where they are reviewed by trained staff to ensure no sensitive or potentially re-identifiable information is released.
What happens if there is a security breach?
SDEs are designed with a “defense in depth” approach to make breaches extremely unlikely, but they also have robust incident response plans. In the event of a suspected breach, immediate action is taken to contain the threat, such as suspending user access or isolating parts of the network. The comprehensive audit trails are then used to conduct a full forensic investigation to understand what happened. Because the data is pseudonymised and encrypted, and cannot be downloaded, the risk of any meaningful data being exposed is minimized. Any security incident would be subject to strict regulatory reporting requirements, such as those under GDPR.
Can patients opt out of their data being used for research?
Yes. In the UK, the National Data Opt-Out allows individuals to choose to stop their confidential patient information from being used for research and planning purposes. All SDEs that use NHS data, such as the NHS England SDE, are required to respect this choice. Before any dataset is made available to researchers, the records of any individuals who have registered an opt-out are removed. This provides a clear and simple mechanism for the public to control how their data is used, further strengthening the trustworthy nature of the SDE ecosystem.
Conclusion: The Future is Secure and Federated
Understanding What is a Secure Data Environment (SDE) is to understand a fundamental shift in data research: one that balances the potential of sensitive data with the protection of individual privacy. SDEs provide unprecedented security through the “bring researchers to the data” model, built on the Five Safes framework and multiple layers of technical and procedural safeguards.
This approach builds the trust needed for groundbreaking research to flourish. The success of platforms like UK Biobank and the NHS’s investment in a national SDE network prove that when researchers can securely access large, linked datasets, medical breakthroughs happen faster.
The future of sensitive data analysis is secure and increasingly federated. This means SDEs across institutions and countries can collaborate by sharing insights and algorithms, while the underlying data remains in its secure location. Instead of moving data, we move the analysis, enabling global research while respecting data sovereignty.
At Lifebit, we are actively shaping this future. Our next-generation federated platforms empower researchers to harness global biomedical data securely and compliantly. Our solutions, including our Trusted Research Environment (TRE) and Trusted Data Lakehouse (TDL), deliver real-time insights and enable secure collaboration across hybrid data ecosystems, ensuring the future of data-driven findy is both groundbreaking and private.
To learn more about how we’re making this vision a reality, explore Lifebit’s Trusted Research Environment.


3 thoughts on “Everything You Need to Know About a Secure Data Environment (SDE)”
Comments are closed.