How to Find Affordable HIPAA-Compliant Web Analytics Without Losing Your Mind

Stop Wasting Millions: Fix Your HIPAA-Compliant Data Analytics in 2026
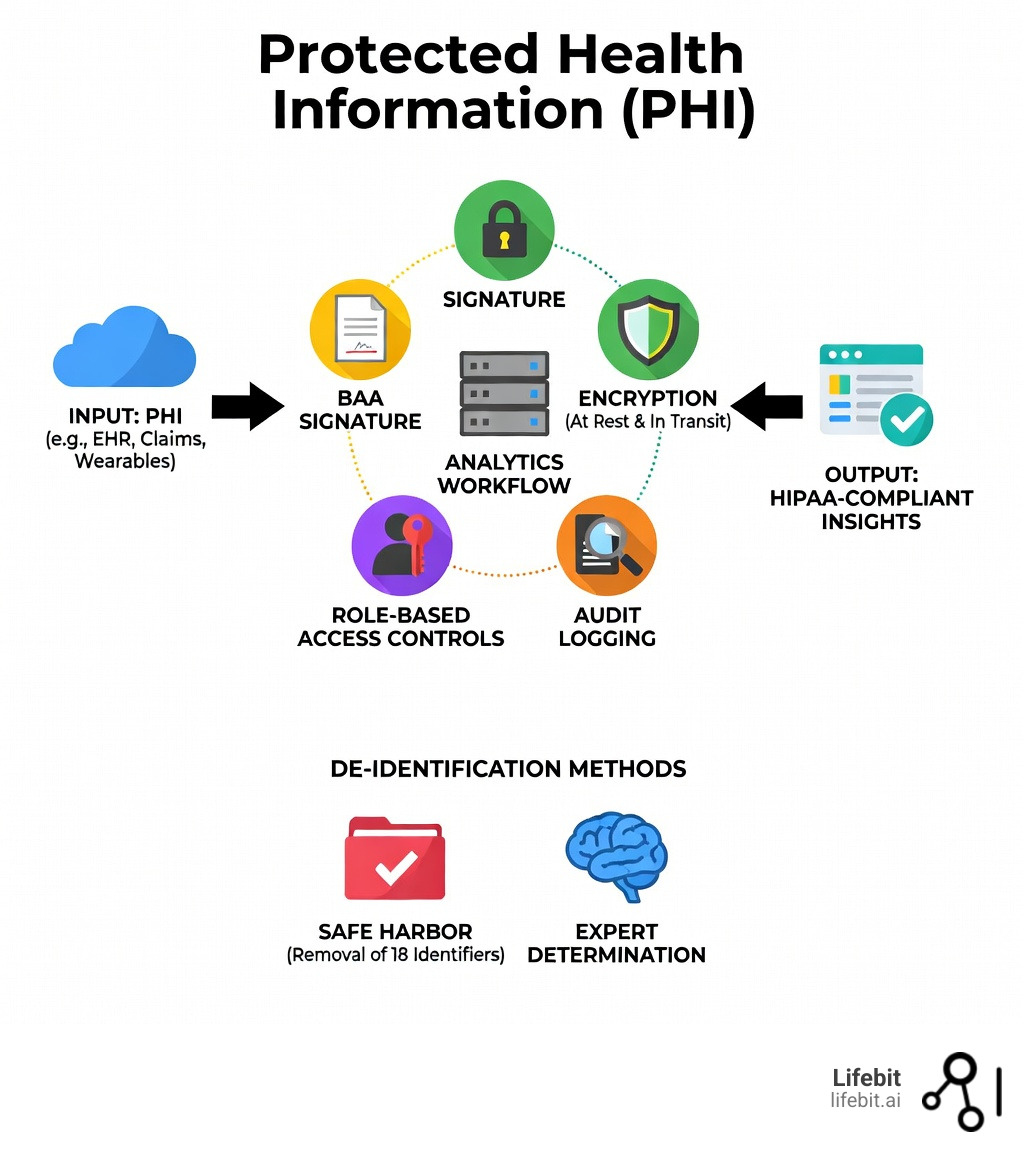
HIPAA-compliant data analytics is the practice of collecting, processing, and analyzing healthcare data while meeting all Health Insurance Portability and Accountability Act (HIPAA) requirements—including Business Associate Agreements (BAAs), encryption, access controls, and audit logging. In 2026, this isn’t just a checkbox; it’s a foundational requirement for any organization looking to leverage AI and machine learning in the clinical space.
Key Requirements for HIPAA-Compliant Analytics:
- Business Associate Agreement (BAA) – Required with any third-party analytics vendor handling Protected Health Information (PHI). This legal contract establishes the chain of liability and ensures the vendor is bound by the same privacy standards as the covered entity.
- Technical Safeguards – Encryption at rest (AES-256) and in transit (TLS 1.3), role-based access controls (RBAC), and comprehensive audit trails that record every instance of data access or modification.
- Administrative Controls – Regular risk assessments, mandatory employee training, and documented incident response plans to mitigate the impact of potential breaches.
- Data De-identification – Utilizing the Safe Harbor method (removing 18 specific identifiers) or Expert Determination (statistical verification) to exempt data from HIPAA regulations for broader research use.
- Physical Safeguards – Ensuring that the physical infrastructure, whether on-premise servers or cloud data centers, is protected against unauthorized physical access and environmental hazards.
- The Minimum Necessary Standard – A core HIPAA principle requiring that only the minimum amount of PHI necessary to accomplish a specific task is used or disclosed.
What Counts as PHI in Analytics:
Any data combining health information with identifiers like names, emails, IP addresses, device IDs, or even web session data from healthcare websites qualifies as electronic PHI (ePHI) under HIPAA. This includes biometric data, full-face photographs, and any unique identifying numbers or codes.
In healthcare, data is sacred—but most organizations are bleeding money trying to analyze it securely. The problem isn’t just compliance. It’s that traditional analytics tools either don’t offer BAAs, leak data to third parties, or force you into expensive enterprise tiers just to meet basic HIPAA requirements. Many legacy systems were built for a pre-cloud era, making them rigid and difficult to integrate with modern AI workflows.
Even seemingly harmless data like IP addresses or form submissions becomes ePHI the moment it touches a covered entity’s system. That means your standard marketing analytics, user tracking, and business intelligence tools could be quietly putting you at risk—and costing you millions in potential HIPAA penalties (up to $1.5 million per violation category annually). Furthermore, the reputational damage from a breach can lead to a permanent loss of patient volume, which is often more costly than the fines themselves.
The good news? You don’t need to choose between security and affordability. Modern HIPAA-compliant analytics platforms use federated architectures, self-hosting options, and privacy-by-design frameworks to deliver real-time insights without moving or exposing sensitive data. These systems allow for “compute-to-data” models where the analysis happens locally, and only aggregated, non-identifiable results are shared.
I’m Maria Chatzou Dunford, CEO and Co-founder of Lifebit, where we’ve built a federated genomics and biomedical data platform that powers secure, HIPAA-compliant data analytics for pharmaceutical organizations and public health institutions across the globe. With over 15 years in computational biology, AI, and health-tech entrepreneurship, I’ve seen how the right infrastructure can open up breakthrough insights while keeping patient data locked down. Our mission is to break down data silos while maintaining the highest standards of privacy and security.
Know your hipaa-compliant data analytics terms:
- AI for precision medicine
- AI for regulatory compliance
Avoid $1.5M Fines: Why HIPAA-Compliant Data Analytics Is Mandatory in 2026
If you are operating in the healthcare space in the USA, UK, or Europe, you already know that HIPAA isn’t just a suggestion—it’s the law. But in 2026, the stakes are higher than ever. Regulatory bodies, including the Office for Civil Rights (OCR), have sharpened their focus on how tracking technologies and analytics platforms handle patient data. The introduction of the HITECH Act and the subsequent Omnibus Rule has significantly increased the potential for civil money penalties, making compliance a financial imperative.
The Privacy Rule protects the “what” (patient names, diagnoses), while the Security Rule dictates the “how” (encryption, firewalls). If a breach occurs, the Breach Notification Rule forces you to go public with your mistakes, notifying affected individuals, the HHS Secretary, and in some cases, the media. Failing to maintain hipaa-compliant data analytics can lead to civil penalties that scale based on your level of negligence—ranging from “did not know” to “willful neglect.” Beyond the fines, a single data leak can shatter the patient trust that took decades to build. We believe that security shouldn’t be an “add-on” feature; it must be embedded in the culture of how we handle data, from the initial collection to the final disposal.

For a deeper dive into the legal landscape, check out our guide on hipaa-compliant data analytics.
What Counts as PHI and ePHI in Your Analytics
Many teams mistakenly believe that if they aren’t recording a Social Security number, they are safe. This is a dangerous myth. Under HIPAA, Protected Health Information (PHI) includes any information about health status, provision of care, or payment that can be linked to an individual. This link can be direct (like a name) or indirect (like a unique patient ID that corresponds to a record in another database).
In the digital world, this becomes electronic PHI (ePHI). According to HHS guidance updated for the modern web environment, ePHI in analytics includes:
- 18 Identifiers: Names, geographic data (smaller than a state), dates (birth, admission, discharge), phone numbers, fax numbers, and emails.
- Metadata: IP addresses and device IDs are considered identifiers if they are collected on a page that relates to a person’s health (like a patient portal, an appointment booking page, or even a blog post about a specific condition).
- Form Submissions: Any data entered into a web form, even if the person isn’t a patient yet. If a user submits a query about “diabetes symptoms,” that interaction is protected.
- Tracking Pixels: Recent enforcement actions have highlighted that third-party tracking pixels (like those from Meta or Google) can inadvertently transmit ePHI to unauthorized vendors if not properly configured or governed by a BAA.
To stay safe, you need a strategy that accounts for all 18 identifiers and the context in which they are collected. Learn more in our HIPAA-compliant analytics guide 2026.
4 Steps to HIPAA-Compliant Data Analytics Without Enterprise Fees
Achieving compliance doesn’t have to cost a fortune, but it does require four non-negotiable pillars. Without these, your analytics stack is a ticking time bomb. Many organizations fall into the trap of paying for “Enterprise” tiers of software just to get a BAA signed, but there are more efficient ways to architect your data flow.
- Business Associate Agreements (BAA): This is a legal contract where your vendor agrees to be liable for protecting your data. It must specify the permitted and required uses of PHI by the business associate. If a vendor won’t sign a Business Associate Agreement, do not give them your data, regardless of how powerful their analytics features are.
- Encryption Everywhere: Data must be encrypted “at rest” (while stored on disks or in databases) and “in transit” (while moving between systems or over the internet). Use industry-standard protocols like AES-256 for storage and TLS 1.3 for communication. Key management is also vital; ensure that encryption keys are stored separately from the data they protect.
- Audit Logging: You must keep a detailed, tamper-proof record of who accessed what data, when they accessed it, and what actions they performed. This is critical for forensic analysis if a security incident occurs and is a requirement for passing a HIPAA audit. Logs should include user IDs, timestamps, source IP addresses, and the specific data elements accessed.
- Role-Based Access Control (RBAC): Not everyone in your marketing or research department needs to see raw patient data. RBAC ensures users only see what they absolutely need to do their jobs (the Principle of Least Privilege). For example, a data scientist might need access to de-identified clinical outcomes, while a billing administrator only needs access to insurance information.
For cloud-specific advice, the Guidance on HIPAA & Cloud Computing is an essential resource for any organization using AWS, GCP, or Azure. These providers operate under a “Shared Responsibility Model,” where they secure the infrastructure, but you are responsible for securing the data you put into it.
Technical Safeguards for Bulletproof Healthcare Insights
To truly protect patient privacy while maintaining data utility, we recommend two primary methods for de-identification as outlined by the HHS:
- The Safe Harbor Method: This involves the removal of all 18 specific identifiers. It’s straightforward and provides a high level of legal certainty, but it can sometimes strip away the context needed for advanced research, such as longitudinal studies that require precise dates.
- Expert Determination: This uses statistical and scientific principles to ensure the risk of re-identification is “very small.” A qualified expert must document the methods used and the results of their analysis. This is often preferred for biomedical research where specific data points (like dates of service or detailed geographic data) are vital for the analysis.
By applying the principle of “Least Privilege” and utilizing advanced de-identification, you ensure that your hipaa-compliant data analytics environment is as secure as possible. You can read more about these methods in the official HHS De-identification Guidance.
How Lifebit Drastically Cuts HIPAA-Compliant Data Analytics Costs
At Lifebit, we realized that the “old way” of doing analytics—moving massive amounts of sensitive data into a central warehouse—was both risky and expensive. The costs associated with data egress (moving data out of a cloud provider) and the storage of redundant datasets can quickly spiral out of control. That’s why we pioneered a federated approach. Instead of moving the data to the code, we move the code to the data.
Our platform, including the Trusted Research Environment (TRE) and R.E.A.L. (Real-time Evidence & Analytics Layer), allows you to perform advanced AI/ML analytics on global biomedical data without it ever leaving its secure home. This drastically reduces the risk of third-party leaks and ensures that data residency requirements are met. In a federated model, the data stays behind the owner’s firewall, and only the analytical insights (the “answers” to the questions) are transmitted back to the researcher.
| Feature | Lifebit Platform | Traditional Analytics |
|---|---|---|
| BAA Support | Included at all levels | Often restricted to “Enterprise” |
| Data Residency | Data stays in your VPC | Data moved to vendor servers |
| Architecture | Federated AI | Centralized Warehouse |
| Compliance | HIPAA, GDPR, SOC2 | Varies by tier |
| Data Egress Costs | Minimal (Insights only) | High (Full data transfer) |
| Security Model | Zero Trust / Federated | Perimeter-based |
Why Most Analytics Tools Put You at Risk (and Cost You More)
Most standard analytics tools are not HIPAA-compliant out of the box. Many common web and product analytics services do not offer a Business Associate Agreement (BAA) for standard deployments and explicitly warn against sending Protected Health Information (PHI) into their platforms. If you use these tools without a BAA, you are in direct violation of HIPAA, even if you attempt to “anonymize” the data yourself.
When you use non-compliant tools, you risk:
- Third-party leaks: Data being shared with downstream processors (for example, advertising or measurement networks) without your knowledge or consent. This is often buried in the “Terms of Service” of free analytics tools.
- Ownership issues: Losing control over who can see or use sensitive insights derived from patient activity. Some vendors claim ownership of the data processed through their systems.
- Regulatory fines: Penalties tied to using tracking technologies on protected pages without the required safeguards. The OCR has recently increased its enforcement actions against healthcare providers using non-compliant tracking pixels.
- Incomplete Data: Because you are afraid of violating HIPAA, you might strip out so much data that the resulting analytics are useless for making business or clinical decisions.
For a comparison of what to look for in a vendor, see our HIPAA compliant analytics platforms guide.
From Marketing to Medicine: How HIPAA-Compliant Data Analytics Saves Lives
HIPAA-compliant data analytics isn’t just about avoiding fines; it’s about saving lives and improving the quality of care. By unlocking the power of healthcare data, organizations can move from reactive treatment to proactive prevention.
- Descriptive Analytics: Hospitals use this to track readmission rates and improve discharge planning. By analyzing historical data, they can identify patterns that lead to patient relapse and intervene before the patient leaves the facility.
- Predictive Modeling: Identifying at-risk populations for chronic diseases like diabetes or heart disease before they require emergency care. Machine learning models can scan EHR data to find early warning signs that a human clinician might miss.
- Discovery Analytics: Researchers use clinical data to find new medication side effects or gene-disease links. This is particularly powerful when combining clinical records with genomic data, leading to the development of targeted therapies.
- Public Health: During emergencies, HIE Public Health Disclosures allow for the legal sharing of PHI to track disease outbreaks while maintaining strict privacy controls. This was instrumental during the COVID-19 pandemic for resource allocation and vaccine distribution tracking.
- Operational Efficiency: Analytics can optimize staff scheduling, reduce wait times in emergency rooms, and manage supply chains for critical medical equipment, ensuring that resources are available when patients need them most.
Scaling HIPAA-Compliant Analytics for Global Research
When we talk about the future of medicine, we’re talking about multi-omic data—combining genomic, clinical, and lifestyle data. Scaling this globally requires a federated model because different countries have different data sovereignty laws (like GDPR in Europe or the Data Protection Act in the UK).
By using Lifebit’s Federated AI platform, biopharma companies and governments can collaborate across borders without the legal and technical nightmare of moving sensitive data. Our Trusted Data Lakehouse (TDL) provides a unified view of disparate datasets, allowing for real-time evidence generation while respecting the HIPAA requirements of the US and the privacy laws of each jurisdiction. This collaborative approach accelerates the pace of drug discovery and brings life-saving treatments to market faster.
Stop the Guesswork: HIPAA-Compliant Data Analytics FAQs
Can I use self-hosted tools to avoid a Business Associate Agreement (BAA)?
No. While self-hosting gives you more control over the infrastructure, if a third-party vendor provides support, updates, or has any access to the system where PHI is stored, they are still considered a Business Associate. You still need a BAA to be fully compliant. Furthermore, the responsibility for maintaining the security of the self-hosted environment (patching, firewalls, physical security) falls entirely on you.
Is de-identified data still covered by HIPAA?
No. Once data is properly de-identified using either the Safe Harbor or Expert Determination method, it is no longer considered PHI and is not subject to HIPAA regulations. However, the process of de-identification itself must be done within a HIPAA-compliant environment. If you are sending PHI to a vendor for the purpose of de-identification, you must have a BAA in place with that vendor.
How does shared responsibility work with cloud providers like AWS or GCP?
Compliance is a team sport. Cloud providers like AWS or GCP are responsible for the security of the cloud (physical servers, hardware, global infrastructure). You are responsible for security in the cloud (configuring firewalls, managing user permissions, encrypting your data, and ensuring your applications are secure). Both parties must sign a BAA. For example, Databricks on AWS requires you to enable specific security profiles and encryption settings to meet your end of the bargain.
What is the difference between a Covered Entity and a Business Associate?
A Covered Entity is a healthcare provider, health plan, or healthcare clearinghouse that transmits health information electronically. A Business Associate is a person or entity that performs certain functions or activities that involve the use or disclosure of PHI on behalf of, or provides services to, a covered entity. Both are directly liable for HIPAA compliance.
Can I use Google Analytics for healthcare websites?
Standard Google Analytics is generally not HIPAA-compliant because Google will not sign a BAA for the free version of the product. While Google Analytics 4 (GA4) offers more privacy controls, using it on pages that collect or display PHI without a BAA and proper configuration is a high-risk activity that has led to recent OCR warnings.
What are the penalties for HIPAA violations in 2026?
Penalties are categorized into four tiers based on the level of culpability. Tier 1 (Unknowing) starts at approximately $137 per violation, while Tier 4 (Willful Neglect – not corrected) can reach over $68,000 per violation, with an annual cap of $2.06 million for identical violations. These amounts are adjusted annually for inflation.
Secure Your Future: Start Your HIPAA-Compliant Data Analytics Journey
Finding affordable hipaa-compliant data analytics doesn’t have to be a nightmare. By focusing on the four pillars of security—BAAs, encryption, audit logs, and access controls—you can protect your patients and your budget simultaneously. As we move further into 2026, the integration of AI into healthcare will only accelerate, making a secure data foundation more critical than ever.
Organizations that prioritize privacy-by-design today will be the ones that lead the industry tomorrow. They will enjoy higher levels of patient trust, lower regulatory risk, and the ability to participate in global research collaborations that are closed to those with non-compliant stacks. The transition to federated analytics is not just a technical upgrade; it’s a strategic move toward a more ethical and efficient healthcare ecosystem.
At Lifebit, we are committed to making global biomedical data accessible and secure. Our federated AI platform is built for the most sensitive data on earth, enabling biopharma and public health agencies to turn raw data into life-saving insights without ever compromising on privacy. We provide the tools to bridge the gap between data silos, allowing for a holistic view of human health that was previously impossible.
Ready to see how federated analytics can transform your research and ensure your organization remains compliant in an evolving regulatory landscape? Explore the Lifebit Platform today and join the revolution in secure healthcare data analytics.

