A Comprehensive Guide to Trusted Clinical Environment Criteria

Stop Waiting 6 Months for Data: Why Trusted Clinical Environments Are Critical

A trusted clinical environment is a highly secure computing platform that enables approved researchers to access and analyze sensitive healthcare data without compromising patient privacy. These environments—also known as Trusted Research Environments (TREs) or Secure Data Environments (SDEs)—solve a critical challenge: open uping the research potential of patient data while upholding the highest standards of security and public trust.
Key characteristics include:
- Secure access controls for authorized, trained researchers only
- Data de-identification to protect patient privacy
- Governed outputs that are screened before leaving the environment
- Comprehensive auditing of all user activities
- Regulatory compliance with frameworks like GDPR and HIPAA
The need is urgent. Current data access processes are painfully slow, with researchers often waiting six months or longer for approval. This delay doesn’t just cause frustration; it can cost lives by slowing the development of new treatments. Furthermore, with only about 52% of the public expressing trust in clinical research, secure and transparent data governance is more critical than ever.
Trust is earned through rigorous safeguards. The widely adopted Five Safes Framework (Safe People, Safe Projects, Safe Settings, Safe Data, and Safe Outputs) provides the foundation, ensuring data serves the public good without exposing patients to risk.
As CEO and Co-founder of Lifebit, I’ve spent over 15 years at the intersection of genomics, data, and AI. Building trusted clinical environments that enable federated analysis across global health data is central to our mission. This guide will walk you through the essential criteria for creating effective and trustworthy research environments.
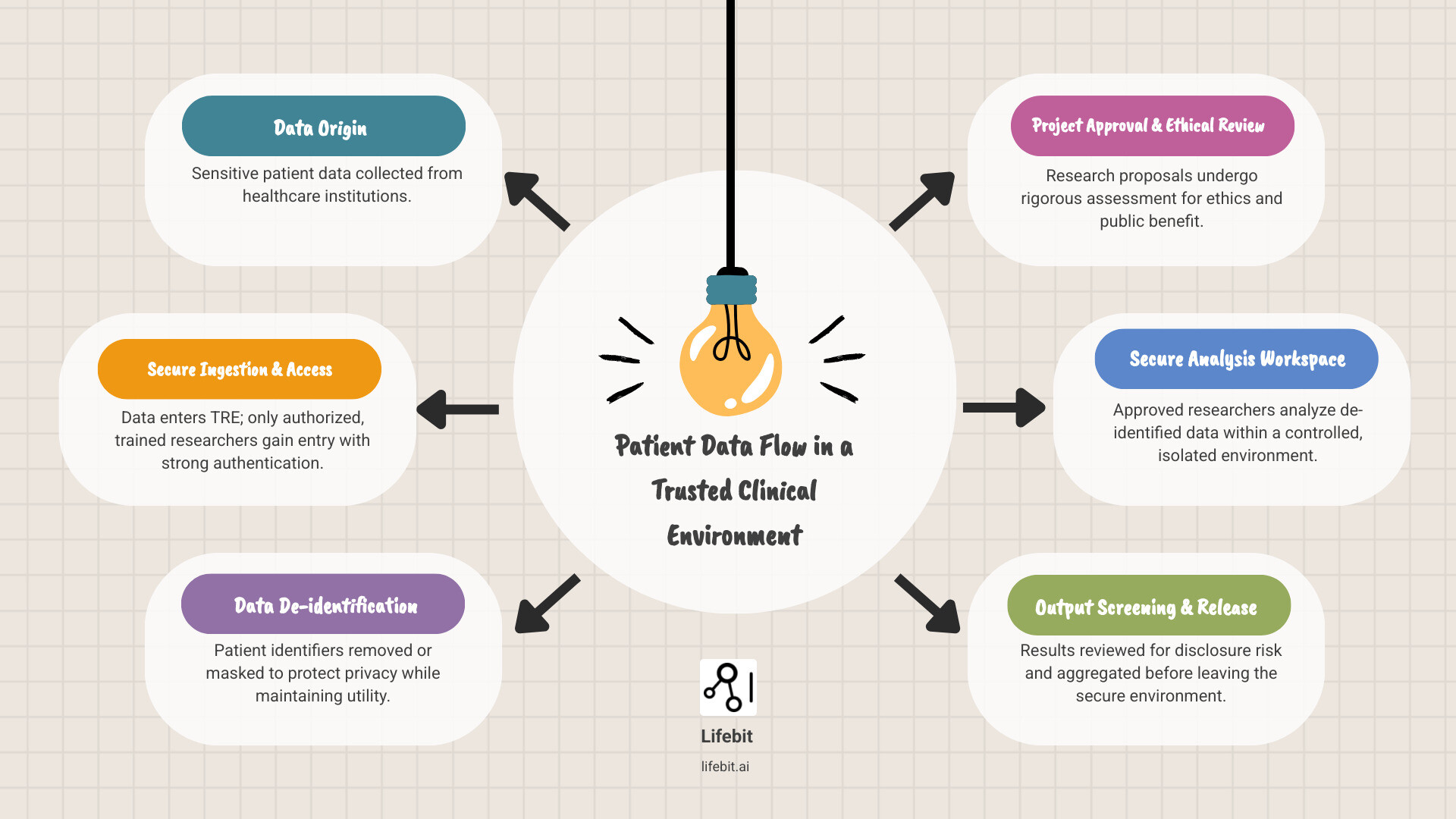
Simple guide to trusted clinical environment terms:
What Is a Trusted Clinical Environment?
The journey from raw patient data to life-saving breakthroughs is paved with complex data. At its heart lies the trusted clinical environment—a carefully designed ecosystem where sensitive patient data can be safely analyzed by approved researchers. Our goal is to accelerate findy without compromising individual privacy.
For too long, groundbreaking research has been stifled by bureaucracy and privacy fears. A trusted clinical environment directly addresses these challenges by providing a secure computing environment that acts as a fortress for patient data, allowing complex analyses while maintaining strict governance. To learn more about what a Secure Data Environment (SDE) entails, explore our detailed guide: What is a Secure Data Environment (SDE)?.
The 5-Pillar Fortress: How to Build an Unbreachable Clinical Environment
A trusted clinical environment is like a fortress with multiple layers of defense. The internationally recognized Five Safes Framework provides this comprehensive protection, addressing every potential vulnerability. These pillars—Safe Settings, Safe Data, Safe People, Safe Projects, and Safe Outputs—are practical principles that turn good intentions into real protection for sensitive patient information. They work in concert to create a holistic security posture where the strength of one pillar reinforces the others.
Let’s explore how each pillar works to create an environment where groundbreaking research can happen without compromising privacy.
Pillar 1: Safe Settings
The foundation of any trusted clinical environment is its digital and physical infrastructure. Safe Settings refers to the creation of a secure computing environment that prevents unauthorized access or data removal. This is not just about firewalls; it involves a multi-layered security architecture. Key components include network segmentation to isolate sensitive data, intrusion detection and prevention systems to monitor for malicious activity, and the use of secure virtual desktop infrastructure (VDI). VDI provides researchers with a controlled analysis workspace, effectively air-gapping them from the raw data and preventing any data from being downloaded to a local machine. The goal is a digital fortress where data can be analyzed but never leaves without strict oversight.
Pillar 2: Safe Data
Safe Data ensures the information itself is treated in a way that minimizes re-identification risk. This begins with robust de-identification or pseudonymization. De-identification involves stripping out direct identifiers like names and addresses, while pseudonymization replaces them with a unique, non-identifiable code, allowing for longitudinal tracking of a patient’s data without revealing their identity. Advanced statistical disclosure limitation techniques, such as k-anonymity (ensuring any individual is indistinguishable from at least k-1 other individuals) or differential privacy (adding mathematical noise to obscure individual contributions), can be applied to further reduce risk. On top of this, data encryption is non-negotiable. Using industry-standard algorithms like AES-256, data must be encrypted both at rest (when stored on servers) and in transit (when moving within the secure network), ensuring that even in the unlikely event of a breach, the data remains unreadable.
Pillar 3: Safe People
Technology alone cannot prevent misuse; human factors are critical. The Safe People pillar ensures that only qualified, trustworthy individuals are granted access. This is not a simple checkbox exercise. It involves a rigorous researcher accreditation process, which may include verifying institutional affiliations, checking credentials, and requiring specialized training on data protection, research ethics, and information security. For example, in the UK, researchers must be familiar with the Caldicott Principles, which govern the use of confidential patient information. Access is granted on a principle of least privilege, and all user activity—every query, every analysis, every login—is logged and audited to ensure accountability and detect anomalous behavior.
Pillar 4: Safe Projects
Hand-in-hand with vetting people is the validation of their work. Safe Projects ensures that data is only used for ethical, scientifically sound research that serves the public good. Every proposed project undergoes a stringent review by an independent oversight body, such as an Institutional Review Board (IRB) or a Data Access Committee (DAC). This committee, composed of scientific, ethical, and lay members, assesses the project’s rationale, methodology, and potential public benefit, weighing it against any residual privacy risks. As the Declaration of Helsinki emphasizes, these boards must be independent and transparent. This pillar guarantees that access to precious patient data is a privilege reserved for research that meaningfully contributes to advancing health and medicine.
Pillar 5: Safe Outputs
The final checkpoint is Safe Outputs. Before any results, tables, or figures can be exported from the secure environment, they must undergo rigorous disclosure control screening to prevent data leakage. This is a multi-stage process. First, automated checks scan for small cell counts (e.g., results based on fewer than 10 individuals) or other potentially disclosive statistics. Then, a trained human reviewer examines the outputs in a secure “airlock”—a holding area where results can be inspected but not removed. This reviewer checks for any information that could, intentionally or not, be used to re-identify individuals or reveal sensitive details. This final safeguard ensures that what leaves the trusted clinical environment is valuable, aggregated insight, not vulnerable, individual-level information.
Trust Isn’t a Feature, It’s a Foundation: Weaving Security, Governance, and Ethics Together
Trust isn’t installed like software; it’s earned through a seamless balance of security, governance, and ethics. With data misuse concerns being a primary reason people hesitate to share their health data, building this trust is the central challenge for modern research. A study by the Wellcome Trust found that transparency about who will use the data and for what purpose is a key driver of public willingness to share.
In a trusted clinical environment, we address these fears with real solutions. Every action is logged, creating a clear audit trail for accountability. Our TREs are designed to align with stringent frameworks like GDPR and HIPAA, but compliance is just the baseline. As a thoughtful BMJ analysis pointed out, trust must be built on transparency and accountability, not assumed. It’s the intersection of robust technical safeguards, transparent governance, and genuine ethical commitment that creates an environment worthy of public confidence. For a deeper understanding, explore the Key Features of a Trusted Research Environments and the critical perspective in the BMJ piece Why Trusted Research Environments Are Not About Trust.
Your Digital Immune System: Essential Technical Safeguards
Technical safeguards are the digital immune system of a trusted clinical environment, creating layered defenses against unauthorized access. These are not just features, but fundamental architectural principles.
- Role-based access controls (RBAC) are foundational, enforcing the principle of least privilege. This means a researcher working on a lung cancer study only gains access to the specific de-identified lung cancer dataset and analytical tools approved for their project. They cannot see or access data related to cardiology or any other project, minimizing the ‘attack surface’ for potential data misuse.
- Multi-factor authentication (MFA) adds a critical verification layer beyond a simple password. By requiring a second factor—such as a code from an authenticator app on a smartphone (something you have) or a biometric scan (something you are)—MFA ensures that a compromised password alone is not enough to grant access to the environment.
- End-to-end encryption scrambles data so it is unreadable to unauthorized parties. This applies to data at rest (stored on disk, encrypted using standards like AES-256) and data in transit (moving across the network, protected by protocols like TLS 1.3). Crucially, this includes robust key management practices to ensure that encryption keys themselves are securely stored and managed.
- Comprehensive auditing and continuous monitoring provide a complete record of all activities. Every login, query, and file access is logged and analyzed in real-time to detect suspicious patterns. This not only enables forensic analysis after an incident but also acts as a powerful deterrent against misuse.
- A formal incident response plan ensures that if a breach does occur, there is a pre-defined, rehearsed process to quickly detect, contain, and mitigate it. This plan outlines steps for eradication, recovery, and post-incident analysis to prevent future occurrences, minimizing harm and maintaining trust.
Beyond the Tech: The Governance and Ethics That Earn Public Trust
While technology provides the tools, governance and ethical frameworks define the rules of engagement and build the social license to operate.
- Data Sharing and Use Agreements (DSAs/DUAs) are legally binding contracts that provide clarity and accountability. These documents go beyond simple permission, specifying the exact data to be used, the approved research purposes, security and privacy obligations, publication policies, and procedures for handling a data breach. They create a clear chain of responsibility for all parties.
- Independent Ethical and Scientific Review by bodies like Institutional Review Boards (IRBs) or Data Access Committees (DACs) is a cornerstone of ethical research. These committees, comprising experts and lay members, provide impartial oversight to ensure a study is scientifically valid and that its societal benefits outweigh any risks to patient privacy. Harmonizing these reviews across multiple institutions, a focus of organizations like the MRCT Center, is a key challenge in facilitating large-scale collaborative research.
- Public and Patient Involvement and Engagement (PPIE) is essential for building a system that reflects societal values. This means moving beyond token gestures to active collaboration. Examples include establishing patient advisory councils to help shape data access policies, co-designing research questions, and creating transparent, easy-to-understand summaries of research findings. This ensures the public are partners in the research process, not just subjects.
- Dynamic Consent Models are transforming the relationship between participants and researchers. Unlike traditional, one-time static consent, dynamic consent platforms give participants a digital interface to manage their preferences on an ongoing basis. They can choose which types of research they support, receive updates on how their data has been used, and even withdraw consent for future use, empowering them with genuine control and fostering a long-term, trust-based relationship.
Open up Your Data’s Potential: The Real-World Impact of a Trusted Environment
The purpose of a trusted clinical environment isn’t just to lock data away, but to open up its immense potential for findy and public good. By creating these secure, ethical spaces, we accelerate research, foster collaboration, and improve health outcomes.

Faster Research, Simpler Governance, Greater Trust: A Win-Win-Win
A trusted clinical environment delivers benefits across the research ecosystem.
- For researchers: It dramatically cuts down the typical six-month wait for data access, enabling faster research cycles. The standardized environment also improves reproducibility, a cornerstone of scientific integrity.
- For institutions: It offers streamlined governance. Instead of navigating a maze of separate agreements, hospitals and companies work within a consistent framework, making complex multi-institutional studies practical.
- For participants: Knowing their data is protected by rigorous safeguards increases willingness to contribute to research. This creates a virtuous cycle: greater trust leads to more participation, which enables more comprehensive research that benefits everyone. Explore the full scope of these advantages in our article on the Advantages of Trusted Research Environments.
From Genomics to Pandemics: How TREs Accelerate Breakthroughs
The impact of trusted clinical environments is especially clear in fields with massive, sensitive datasets. In genomics, organizations like Genomics England house petabytes of data from over 135,000 whole genomes. Analyzing this securely is only possible within a TRE. The Genomics England Research Environment used this model to accelerate our understanding of rare diseases and cancer.
In public health, TREs provide the infrastructure to analyze real-world data at scale. During the COVID-19 pandemic, they were essential for monitoring vaccine efficacy and safety across diverse populations, allowing agencies to make evidence-based decisions quickly while protecting privacy.
Biobanks also thrive within TREs, allowing researchers to securely access data from multiple repositories for large-scale studies. For those interested in active clinical studies, the NIH provides a comprehensive registry: Explore clinical studies. These examples show that a trusted clinical environment is not just about data management; it’s about enabling the next generation of life-saving research.
Centralized vs. Federated: Choosing the Right Architecture for Your TRE
The architecture of a trusted clinical environment is evolving. As data becomes more distributed across institutions and borders, we need models that can keep pace. Today, a lack of standardization across TREs creates friction, forcing researchers to navigate a maze of different governance structures and causing months-long delays. This fragmentation hinders the seamless data sharing needed to advance medicine, particularly for rare diseases or global health challenges that require massive, diverse datasets.
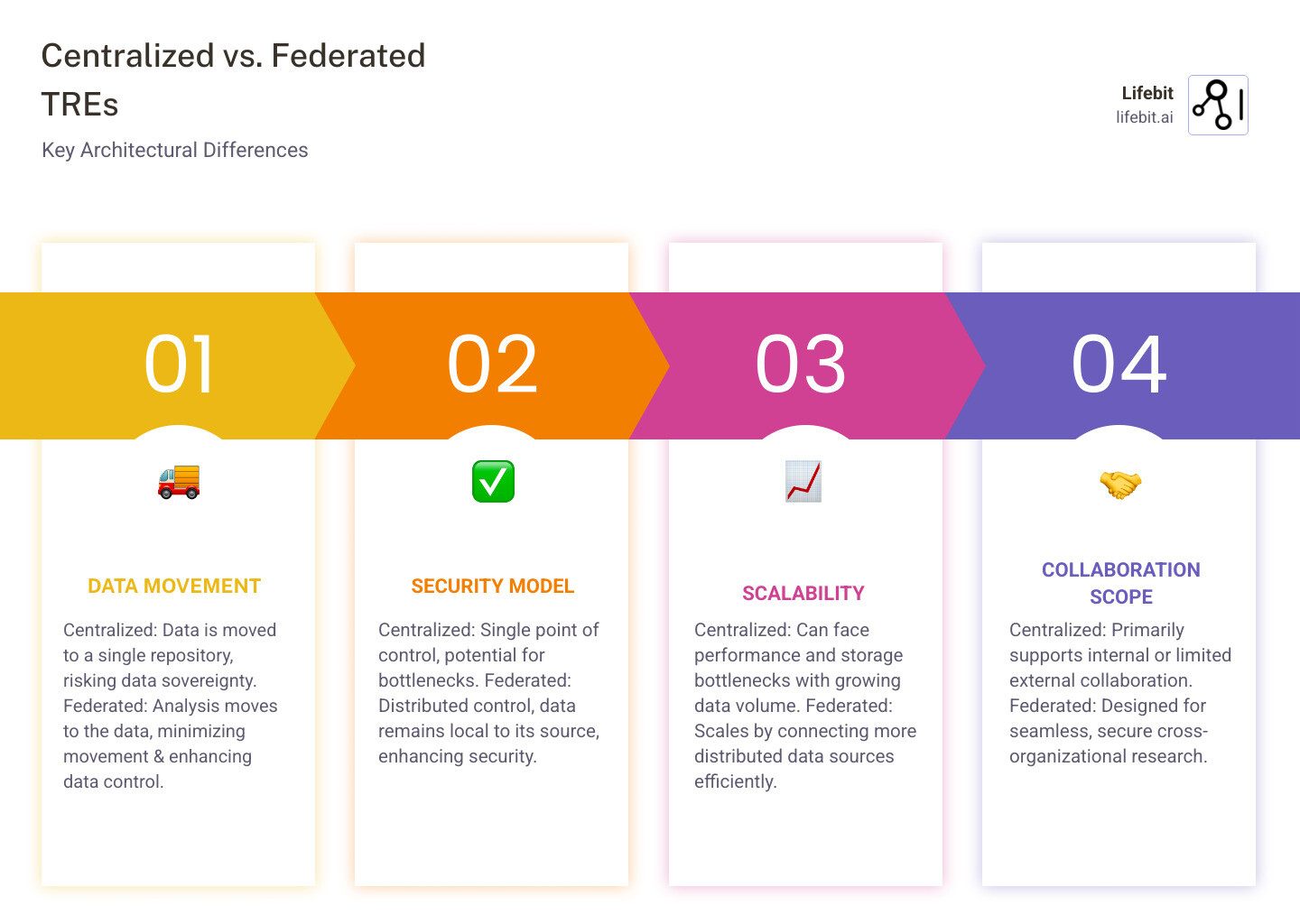
The Old Way vs. The New Way: Why Federated Models Are the Future
For years, the centralized model was standard. In this approach, sensitive data is copied and moved from multiple sources into a single, secure data lake or warehouse for analysis. While conceptually simple, this model presents significant drawbacks. Moving massive datasets is costly, time-consuming, and creates a high-value target for cyberattacks—a single breach could compromise data from numerous institutions. Furthermore, it raises complex legal and ethical questions about data sovereignty, as moving data across regional or national borders can violate regulations like GDPR.
The future is federated. Instead of bringing data to the analysis, we bring the analysis to the data.
In a federated TRE, patient data remains securely within the originating institution’s firewall. When a researcher wants to run an analysis, their analytical code (often packaged in a secure container) is sent to each data location. The analysis executes locally on the data, and only the aggregated, non-identifiable results (e.g., a statistical model or p-values) are returned to the researcher. This model, also known as distributed analysis, inherently respects data sovereignty and minimizes privacy risks by eliminating the movement of raw data.
Lifebit’s patented federated architecture was designed for this model. By deploying TREs directly where data is held, we enable true federated data analysis, simplifying cross-organizational collaboration without the complexity of data aggregation. To understand how this works, explore our insights on the Federated Trusted Research Environment.
Navigating the Problems: Overcoming Key TRE Implementation Challenges
Building a trusted clinical environment, whether centralized or federated, is not a plug-and-play task. Organizations face significant hurdles that require careful planning and expertise.
- Technical Complexity: Integrating diverse data sources is a major challenge. Healthcare data exists in myriad formats (EHRs, imaging, genomics), requiring significant effort in data harmonization. Adopting standards like the OMOP Common Data Model can help, but implementation is resource-intensive. Furthermore, the platform must provide a powerful and flexible suite of analytical tools while maintaining strict security, a difficult balancing act.
- Stakeholder Buy-in: A TRE impacts many groups, and success depends on earning their trust. Data custodians (hospital IT and legal departments) are often risk-averse and need assurance that security is uncompromised. Researchers need an environment that is powerful and easy to use, not one that hinders their work. Most importantly, patients and the public must be convinced that the system is ethical and serves their interests, which requires transparent communication and demonstrable accountability.
- Regulatory Navigation: The legal landscape is complex and constantly evolving. Frameworks like GDPR in Europe and HIPAA in the US impose strict requirements on data handling. Emerging initiatives like the European Health Data Space (EHDS) aim to facilitate cross-border data use for research but also introduce new compliance obligations. Navigating these rules, especially for international collaborations, requires specialized legal and regulatory expertise.
- Cost and Sustainability: Establishing a TRE involves significant upfront investment in infrastructure, software, and specialized personnel. Beyond the initial build, there are substantial ongoing operational costs for maintenance, security monitoring, user support, and compliance audits. Organizations must develop a clear sustainability plan from the outset. This could involve a mix of institutional funding, overheads from research grants, or a fee-for-service model for commercial users, ensuring the TRE remains a viable resource for the long term.
Despite these challenges, the benefits far outweigh the obstacles. The key is a strategic approach and partnering with experienced providers. Our whitepaper, Top 10 Best Practices for Building a Trusted Research Environment, offers concrete strategies for addressing these issues.
Your Top 3 Questions About Trusted Clinical Environments, Answered
If you’re new to trusted clinical environments, you likely have questions. Here are clear, straightforward answers to the most common ones.
Q1: TRE vs. SDE—What’s the Difference?
There is virtually no difference. The terms “Trusted Research Environment (TRE)”, “Secure Data Environment (SDE)”, and “Data Safe Haven” are largely interchangeable. They all describe a highly secure, controlled computing platform for analyzing sensitive health data without compromising patient privacy.
The term used often depends on regional preference. In the UK, for example, the NHS has increasingly adopted “Secure Data Environment (SDE).” Regardless of the name, the core function is identical: providing a protected digital space for secure research. To explore the nuances, check out our guide: What is a Secure Data Environment (SDE)?
Q2: Can a TRE Really Cut Down the 6-Month Wait for Data?
Yes. A trusted clinical environment is specifically designed to slash the traditional six-month or longer wait for data access. Because the secure environment and its access protocols are pre-approved, the process is dramatically streamlined.
While steps like protocol validation (approx. 30 working days), contracting (4 weeks), and data specification (8-12 weeks) still require careful attention, the overall process is far more efficient. A TRE eliminates redundant security reviews for each new project, getting researchers to work faster while maintaining rigorous oversight.
Q3: Are TREs Only for Academic Research, or Can Commercial Firms Use Them?
Absolutely. A trusted clinical environment is essential infrastructure for commercial research by pharmaceutical and biotech firms developing new treatments.
The same rules apply to all: any research, whether commercial or academic, must demonstrate public benefit and pass the same rigorous ethical reviews. There are no shortcuts. These public-private partnerships are vital for translating findings into real-world applications. Furthermore, revenue from approved commercial access can help fund the TRE’s ongoing maintenance, creating a sustainable model that benefits the entire research community. Learn more in our article on Trusted Research Environments for Data Commercialization.
The Future is Federated: Building the Next Generation of Secure Research
The world of healthcare research is changing. An explosion of data, combined with the power of AI, promises a new era of findy. But this potential can only be realized if we can access data safely and responsibly. The trusted clinical environment is the foundation upon which this future will be built.
Global collaboration is now essential, requiring interoperable TREs that work across borders and regulatory frameworks like the European Health Data Space (EHDS). At the same time, patient empowerment through dynamic consent and greater transparency is becoming the norm. Without public trust, we won’t have the data needed for medical breakthroughs.
Lifebit is proud to lead this change. Our next-generation federated AI platform enables secure, real-time access to global biomedical data without compromising privacy. Our unique federated architecture brings the analysis to the data, rather than moving sensitive data around. This allows pharmaceutical companies, governments, and public health agencies to collaborate on large-scale research and pharmacovigilance without ever compromising data sovereignty. It’s secure collaboration at scale, powered by advanced AI and built-in federated governance.
The future we’re building is one where medical breakthroughs happen faster, researchers spend more time making findies, and patients trust that their data is protected. This isn’t science fiction—it’s happening now. To learn how our solutions are powering the next generation of secure, collaborative research, explore Learn more about Lifebit’s Trusted Research Environment. Together, we can open up the potential of health data to change lives.

